What Is Social Engineering?
social engineering is not a cyber attack.Social engineering is the tactic of manipulating, influencing, or deceiving a victim in order to gaining control/access over a computer system and servers, or to steal personal and financial information and many more thing of victims,company and organization. Social engineers, those who exploit social engineering attacks, exploit this, essentially “hacking” humans.
How does social engineering work?
In a typical social engineering attack, a cybercriminal will communicate with the intended victim by saying they are from a trusted organization. In some cases, they will even impersonate a person the victim knows.
For examples:
Imagine someone receives a generic message warning them of fraudulent activity on their bank account. They might ignore it, thinking it’s a spam message. However, if the message appears to come directly from their bank, with accurate branding and a familiar tone, they are more likely to pay attention.This message more make believable,the attacker might include specific details that resonate with the victim’s recent activities.Scenario,it could mention a suspicious charge from a country they recently visited or a duplicate charge for a bill they have already legitimately paid. This specific key information increases the sense of urgency and legitimacy, increasing the likelihood that the victim will engage.and this message is increase in u leverage emotional triggers such as fear and urgency.
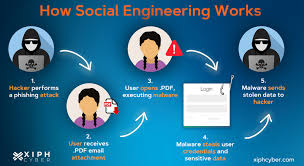
Types of social engineering attacks?
Cyber criminals often employ social engineering tactics to exploit human vulnerabilities. These attacks can take various forms, such as text messages, phone calls, or in-person interactions.Social engineering attacks come in many different forms and can be performed anywhere where human interaction is involved. Let’s explore some of the common methods used in each category.
Phishing: This process to attempting the acquire sensitive information such as usernames, passwords, and credit card details by misleading by using bulk email, SMS text messaging, or by phone. Phishing messages create a sense of urgency, curiosity, or fear this message triggered emotion. The message will prod victims into revealing sensitive information, clicking on links to malicious websites, or opening attachments that contain malware.
Baiting: A type of social engineering attack where a scammer uses a false promise to lure a victim into a trap which may steal personal and financial information or inflict the system with malware. The trap could be in the form of a malicious attachment with an enticing name.
Example: USB baiting sounds a bit unrealistic, but it happens more often than you might think. Essentially what happens is that cybercriminals install malware on to USB sticks and leave them in strategic places, hoping that someone will pick the USB up and plug it into a corporate environment, there by unwittingly unleashing malicious code into their organization.
Tailgating: Also known as “piggybacking”. Its physical breach where an unauthorized person manipulate and create their way into a restricted or employee only authorized area and they use of social engineering tactics. The attacker might impersonate a delivery driver, or custodian worker. Once the employee opens the door, the attacker asks the employee to hold the door, thereby gaining access to the building.
Dumpster Diving: A scammer will search for sensitive information e.g., bank statements, pre-approved credit cards, student loans, other account information, in the garbage when it hasn’t been properly sanitized or destroyed.
Rogue Wi-Fi Networks: Attackers set up a fake Wi-Fi to intercept data from unsuspecting victims.
If u know about of all types of social engineering u can search on internet.
It’s Social Engineering Case Studies in Companies from internet
Twitter – 2020
In July 2020, hackers gained access to Twitter’s (now known as X) internal systems and compromised high-profile accounts, including those owned by Barack Obama, Elon Musk, Bill Gates, and more. The hackers used social engineering tactics to manipulate employees and gain access to internal tools. They posted fraudulent messages from these accounts promoting a Bitcoin scam, asking people to send cryptocurrency to a specified address.
The incident exposed various security weaknesses and brought into question the company’s ability to protect high-level accounts. This incident damaged users’ trust in Twitter’s security measures, as users and experts criticized the company’s response. The attack caused a temporary drop in Twitter’s stock price and led to a federal investigation.
Uber – 2022 and 2016
In 2020, an attacker used social engineering to compromise Uber‘s systems. The individual who admitted to the hack informed The New York Times that they had sent a text message to an Uber employee, posing as corporate IT personnel. Through social engineering, the attacker convinced the employee to disclose a password, granting the hacker entry into Uber’s systems.
The attacker claimed to have access to internal messaging services, databases, source code and emails.
This was not Uber’s first breach. After a previous attack in 2016, the former Chief Security Officer (CSO) was convicted of federal charges for covering up a data breach involving millions of uber user records. This attack was not related to social engineering. According to reports, developers uploaded code containing credentials to GitHub, where attackers found them and used them to access Uber’s systems, resulting in a data breach affecting 57 million riders.
Uber was fined $1.2 million by British and Dutch data regulators for weak security practices exposed by the attack.
Sony Pictures – 2014
A criminal group named the “Guardians of Peace” targeted Sony Pictures Entertainment. The attack resulted in the theft and release of sensitive company data, including emails, employee information, and unreleased films. According to the US Government, the attackers used phishing to gain access to Sony’s network.
The breach significantly damaged Sony’s reputation, as leaked emails revealed controversial conversations among executives and exposed internal conflicts. The attack cost Sony millions of dollars in remediation efforts, legal settlements, and lost revenue from leaked films. Additionally, the incident prompted legal investigations and raised concerns about cybersecurity vulnerabilities in the entertainment industry.
Social Engineering Prevention
Preventing social engineering attacks requires a combination of awareness, vigilance, and security best practices. Here are some key ways to protect yourself:
1. Awareness and Training like as (e.g., phishing, pretexting, baiting, tailgating).
2. Only permission gives Verify Identities
3. Be Cautious with Emails and Links
- Do not click on unknown or suspicious links.
- Check for red flags in emails:
- Urgency or threats
- Spelling errors
- Unfamiliar sender addresses
- Generic greetings like “Dear User”
- Hover over links to inspect their destination before clicking.
4. Use Strong Authentication
5. Secure Personal Information
6. Phone and In-Person Scams
7. Report Suspicious Activities
- If you suspect a social engineering attempt, report it to your organization’s security team or relevant authorities.
- Keep records of suspicious emails or calls for future reference.
8. Use Security Tools
- Install email filters to detect phishing attempts.
- Use endpoint security solutions to prevent malware infections.
- Enable browser security features to detect malicious sites.
- Would you like tips on how to practice identifying social engineering attacks?