The process of learning about a target online application in order to find any potential flaws or vulnerabilities is known as web application reconnaissance. By mapping out the attack surface using both passive and active tactics, security experts can fortify defenses before they are exploited.
Because it enables proactive protection methods by assisting in the early identification of potential vulnerabilities, web application reconnaissance is essential to cybersecurity. Security experts may avoid breaches, reduce risks, and guarantee strong defense against online attacks by comprehending the architecture and vulnerabilities of an application.
Types of Web Application Reconnaissance
Passive Reconnaissance: Gathering publicly accessible data on a target—like domain names, IP addresses, or social media activity—without making direct contact is known as passive reconnaissance. Without warning the target, it aids in understanding them.
Active Reconnaissance: Active reconnaissance, such as scanning or testing for flaws, entails working directly with a web application to find vulnerabilities. Although it offers more thorough insights, it might also warn the target of possible dangers.
Tools Used for Reconnaissance
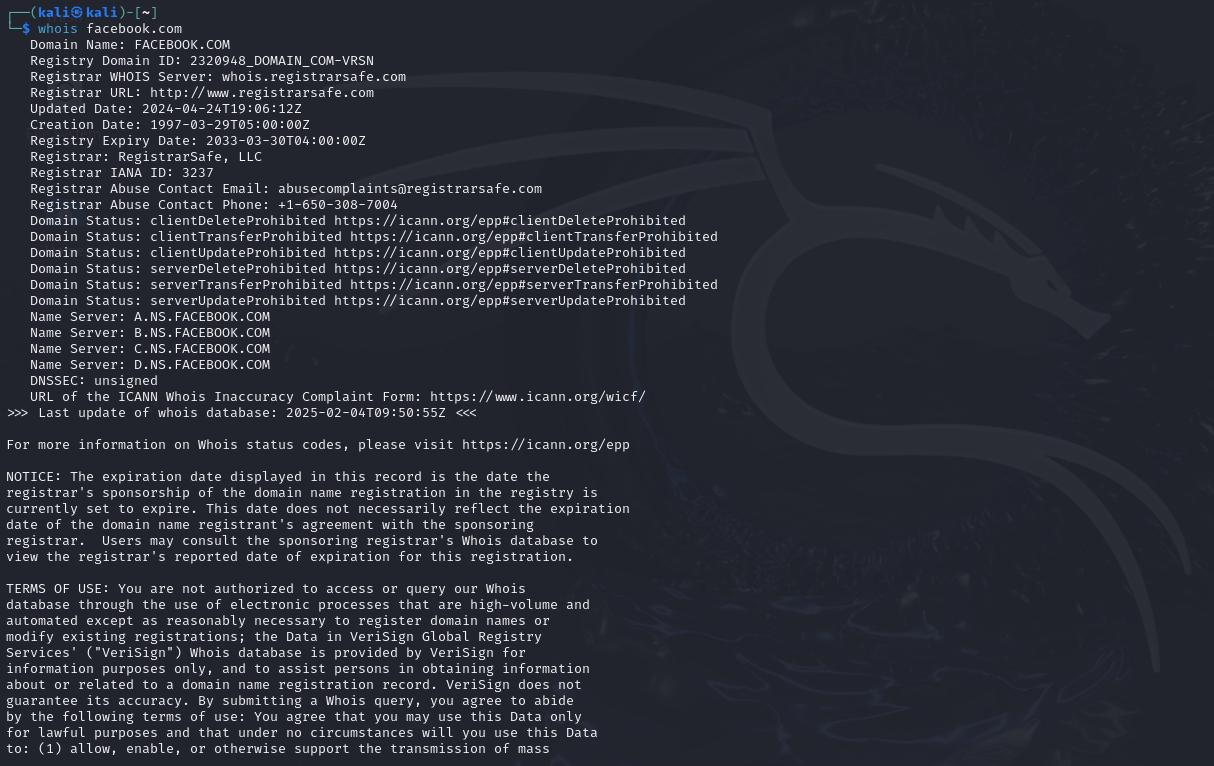
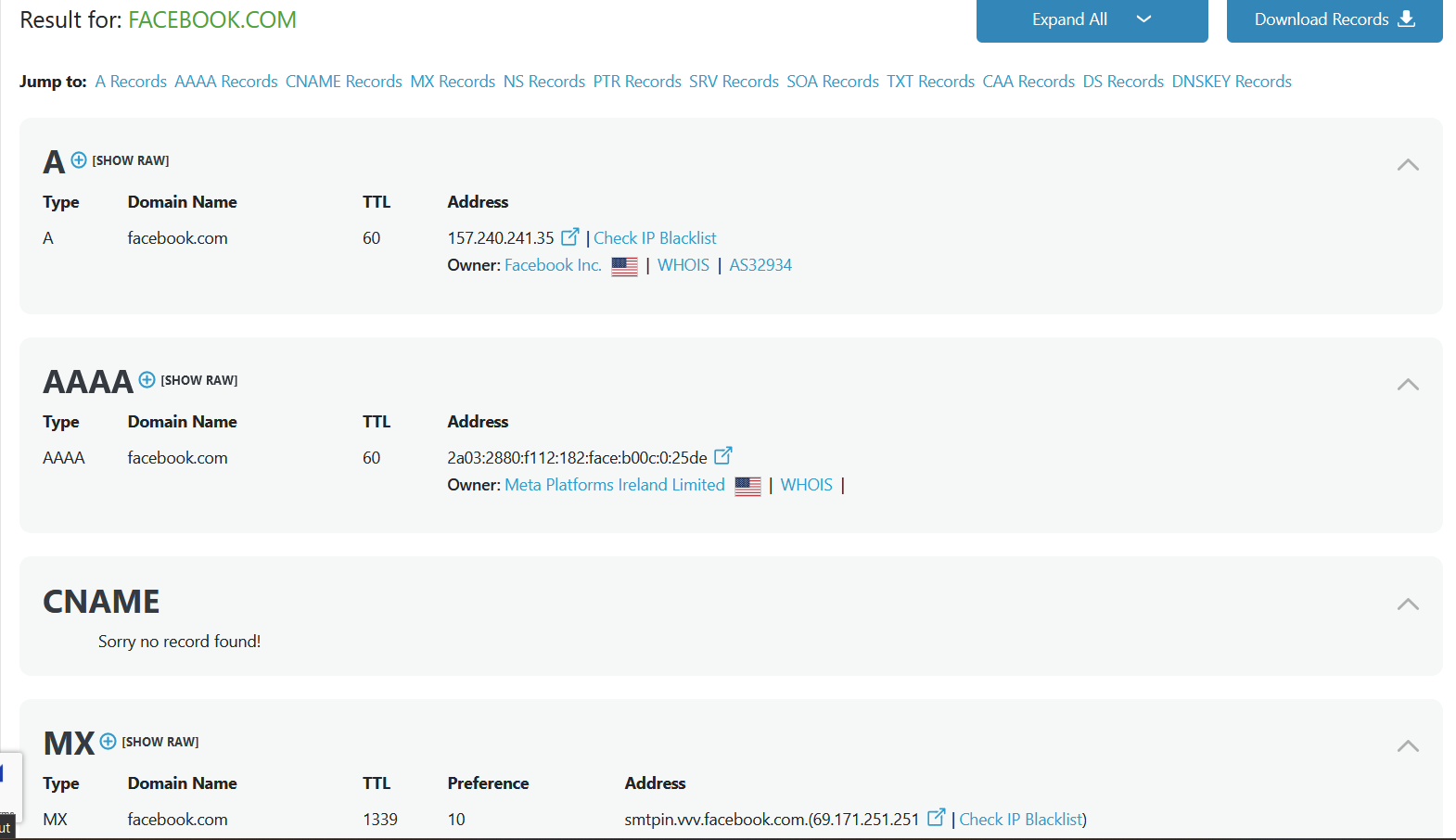
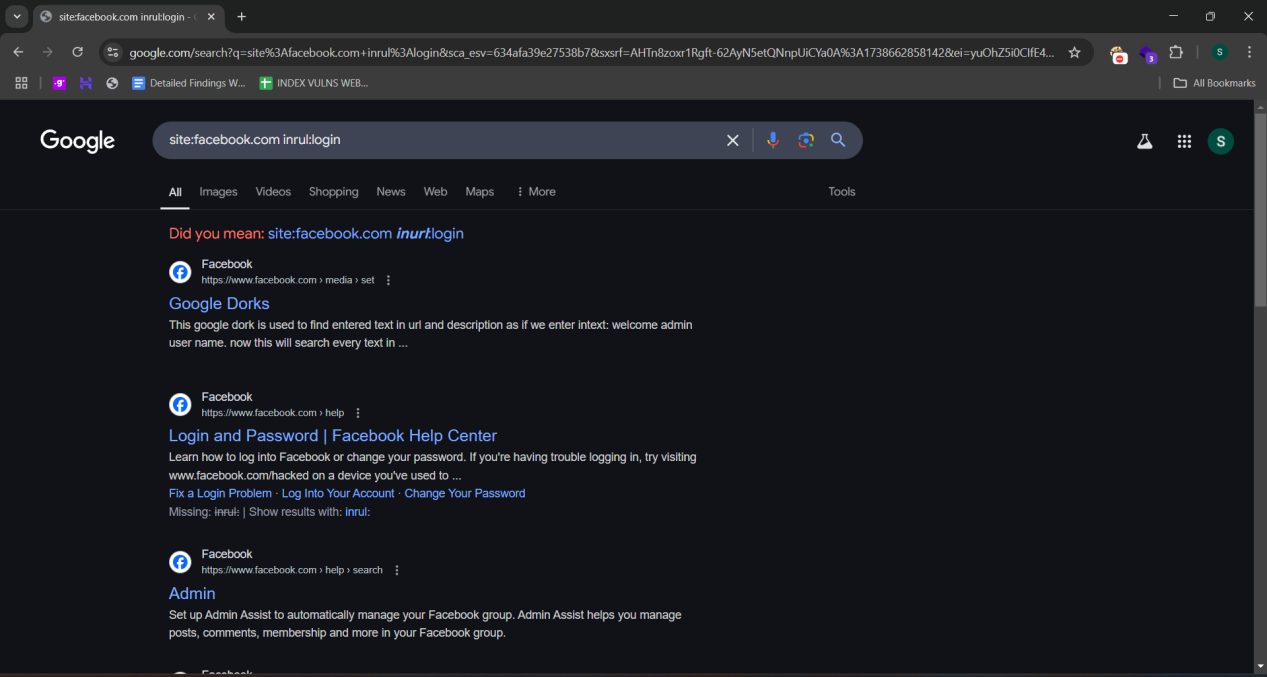
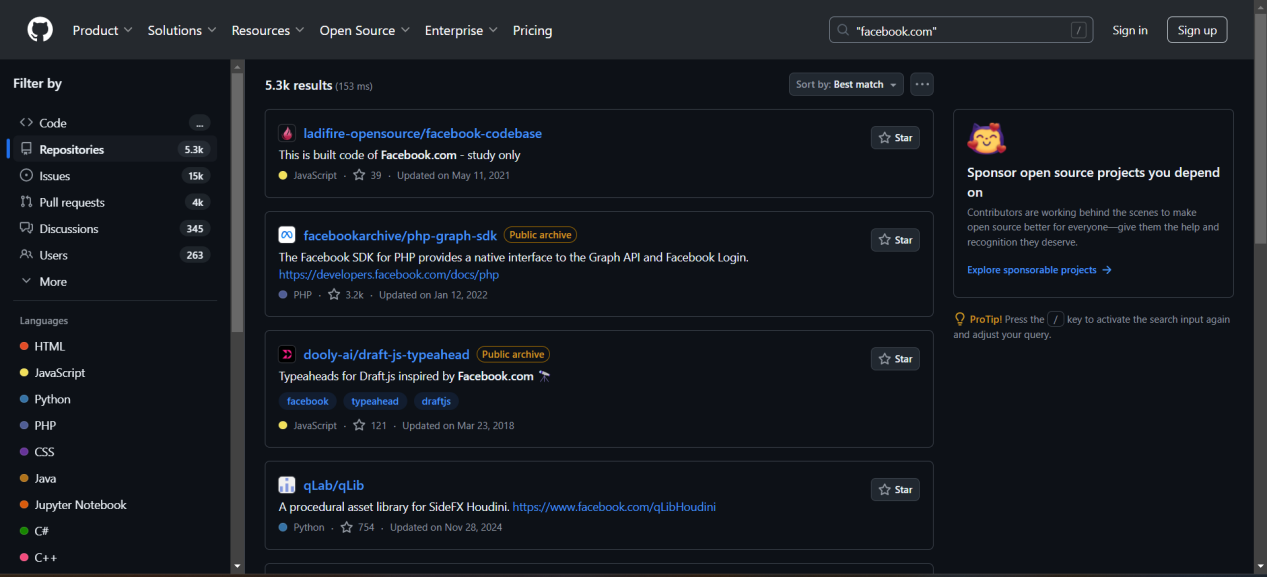
Passive Tools: Whois, DNS Lookup, Google Dorking, Github Dorking, etc.
Whois
DNS Lookup
Google Dorking
Github Dorking
Active Tools: Nmap, Burp Suite, Subfinder, ffuf, etc.
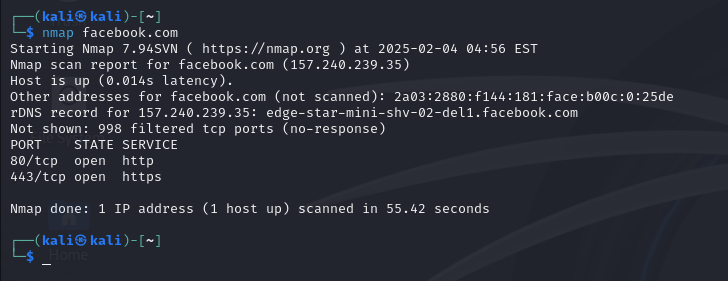
Nmap
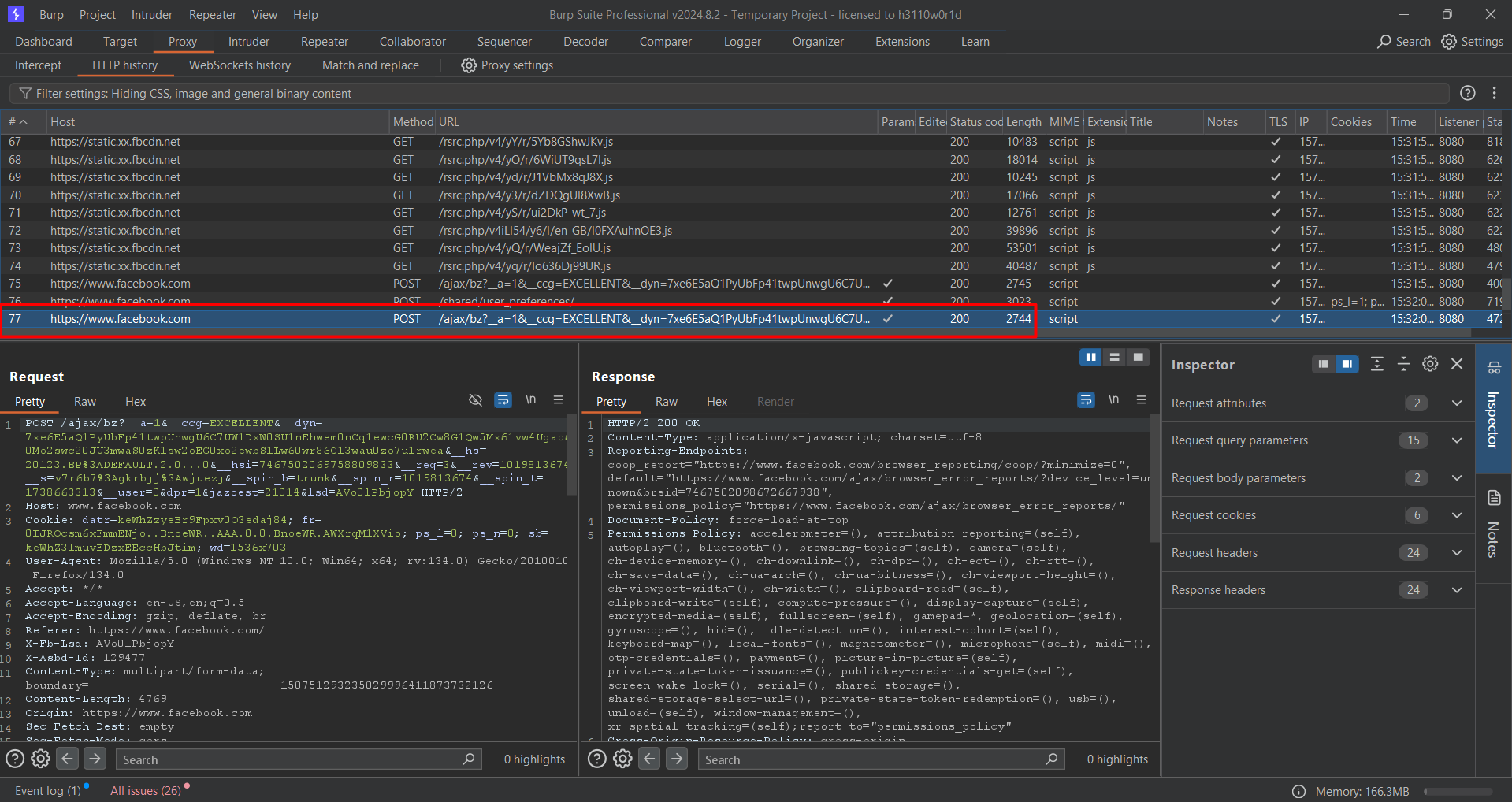
Burp Suite
FFUF
Phases of Web Application Reconnaissance
Information Gathering: Finding important resources, such as domains, subdomains, IP addresses, and network settings, is part of the information gathering process. This fundamental stage aids in the creation of a thorough target map, which directs subsequent attack surface and vulnerability assessments.
Service and Version Detection: Finding the web server software, technologies, and frameworks that a web application uses is known as service and version detection. This aids in evaluating potential weaknesses linked to certain iterations or antiquated technologies.
Vulnerability Identification: To find possible security holes in a web application, vulnerability identification entails examining its attack surface. This procedure aids in setting priorities for potentially exploitable regions, directing cleanup activities, etc.
Reconnaissance Techniques
- Footprinting: Collecting publicly available information
- Subdomain Enumeration: Finding subdomains linked to the main application
- Web Crawling and Spidering: Exploring all available pages and directories