A Beginner’s Guide to Firewalls and Network Safety
Firewalls are a very important part of any organization’s security infrastructure. They act as a barrier between trusted networks and harmful sources.
This Module helps to know about firewalls — their functionality, configurations, and strategies to bypass or enhance their security, giving ethical hackers the knowledge to test and secure these systems.
Let’s explore what this module offers and why firewalls are the firstline of network defense.
What is a Firewall?
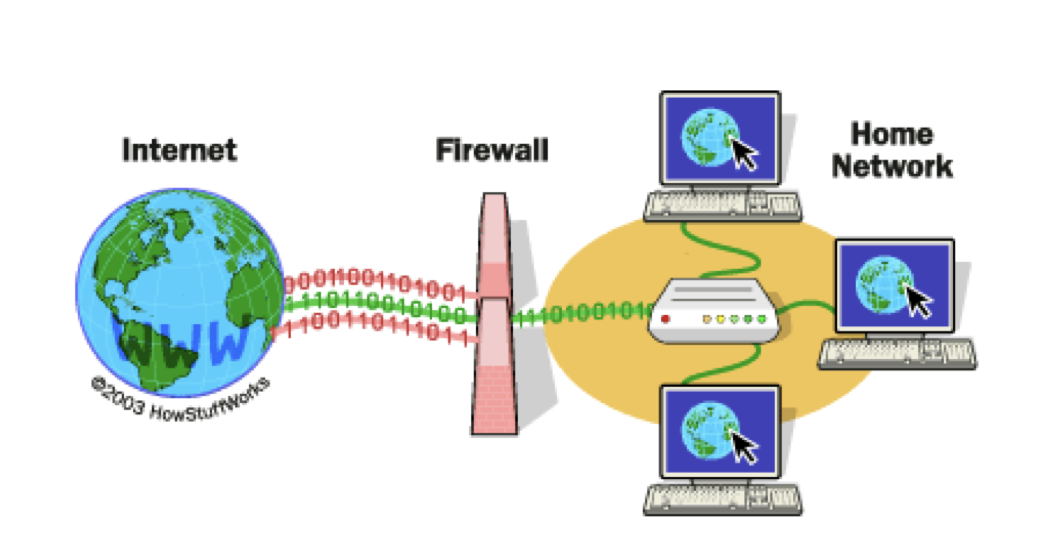
A firewall is a security device or software that monitors and controls incoming and outgoing traffic based on predefined rules. It works as a digital gatekeeper which allows legitimate traffic while blocking malicious or unauthorized access. Firewalls are essential for securing networks from threats like malware, hackers, and unauthorized users.
Main Topics :
#Types of Firewalls
1. Packet-Filtering Firewalls
This firewall examine individual packets of data against a set of predefined rules. These rules are based on criteria like source and destination IP addresses, ports, and protocols.
- How It Works:
- Filters traffic based on headers in each packet.
- Blocks or allows packets based on the rule set (e.g., block port 23 for Telnet).
- Strengths:
- Simple and fast.
- Effective for basic traffic control.
- Limitations:
- Cannot analyze packet content or track sessions.
- Vulnerable to attacks like IP spoofing.
2. Stateful Inspection Firewalls
They track the state of active connections and use this context to make filtering decisions.
- How It Works:
- Maintains a state table to monitor ongoing connections.
- Only allows packets that are part of established sessions.
- Strengths:
- Provides better security by understanding connection states.
- Prevents unauthorized access while allowing legitimate traffic.
- Limitations:
- More resource-intensive than packet-filtering firewalls.
- Requires more configuration and management.
3. Proxy Firewalls
These firewalls work between users and the server. All traffic passes through the proxy, which analyzes and filters it before forwarding.
- How It Works:
- Inspects traffic content.
- Masks the user’s IP address, enhancing anonymity.
- Strengths:
- Offers detailed content inspection and robust security.
- Can block specific content or applications, such as websites or downloads.
- Limitations:
- Slower compared to other types due to in-depth analysis.
- May require significant configuration and maintenance.
4. Next-Generation Firewalls (NGFWs): Combine traditional firewalls with advanced features like deep packet inspection, intrusion prevention, and application-level filtering.
#Firewall Architectures
- Network-Based Firewalls: Deployed at network perimeters to secure large-scale systems.
- Host-Based Firewalls: Installed on individual devices to protect them directly.
- Cloud Firewalls: Secure virtual environments and cloud-based resources.
#How Firewalls Work
A firewall enforces security policies through Access Control Lists and predefined rules.
- Inbound and Outbound Filtering: Monitoring data entering or leaving the network.
- Rule Creation: Setting up rules based on IP addresses, ports, and protocols.
- Zones and Interfaces: Configuring trusted, untrusted, and DMZ zones for better segmentation.
#Firewall Evasion Techniques
Ethical hackers need to understand how attackers bypass firewalls to secure them better.
1. Tunneling
Tunneling involves making malicious traffic within trusted protocols like HTTP or HTTPS, making it appear harmless. Since firewalls often allow these protocols for regular web traffic, malicious payloads can pass undetected.
- Defense:
- Use deep packet inspection to analyze the content of traffic.
- Restrict unnecessary protocols and monitor for unusual traffic patterns.
2. Spoofing
Spoofing involves manipulating packet headers, such as source or IP addresses, to disguise the traffic or bypass rules. This can trick firewalls into allowing unauthorized traffic.
- Defense:
- Implement strict IP validation and anti-spoofing measures.
3. Misconfiguration Exploitation
Attackers can exploit overly permissive firewall rules such as open ports or weak rules, provide an easy way to bypass security controls.
- Defense:
- Regularly review and update firewall rules.
- Use automated tools to audit configurations.
4. Encryption
Encryption is used to hide malicious traffic within encrypted connections, such as HTTPS or VPNs. Since the content is encrypted, firewalls cannot inspect the payload without decryption.
- Defense:
- Implement SSL/TLS inspection to analyze encrypted traffic.
#Firewall Hardening and Countermeasures
- Ensuring firmware and rules are up-to-date.
- Avoiding overly permissive rules and keeping ACLs clean.
- Using VLANs and zones to isolate sensitive resources.
- Combining firewalls with IPS for better threat detection.
- Continuously analyzing firewall logs to detect suspicious activities.
Conclusion
This module guides us to understand, configure, and test firewalls. Whether you’re learning about basic packet-filtering firewalls or advanced next-gen firewalls, this module ensures you’re equipped with the skills to identify vulnerabilities and defend against threats.
Firewalls just help you to detect malicious entry in your system but you have to remove it from your system yourselves.
A Beginner’s Guide to Firewalls and Network Safety Read More »