Python: Install Python on your Windows machine.
Nox Player: Install Nox Player, an Android emulator for Windows.
Download and Configure:-
1. Check Python Installation: Open command prompt and type the following command to check if Python is installed:
“python –version”
2. Install Frida-Tools: Open PowerShell and install Drozer using pip3:
“pip3 install drozer”
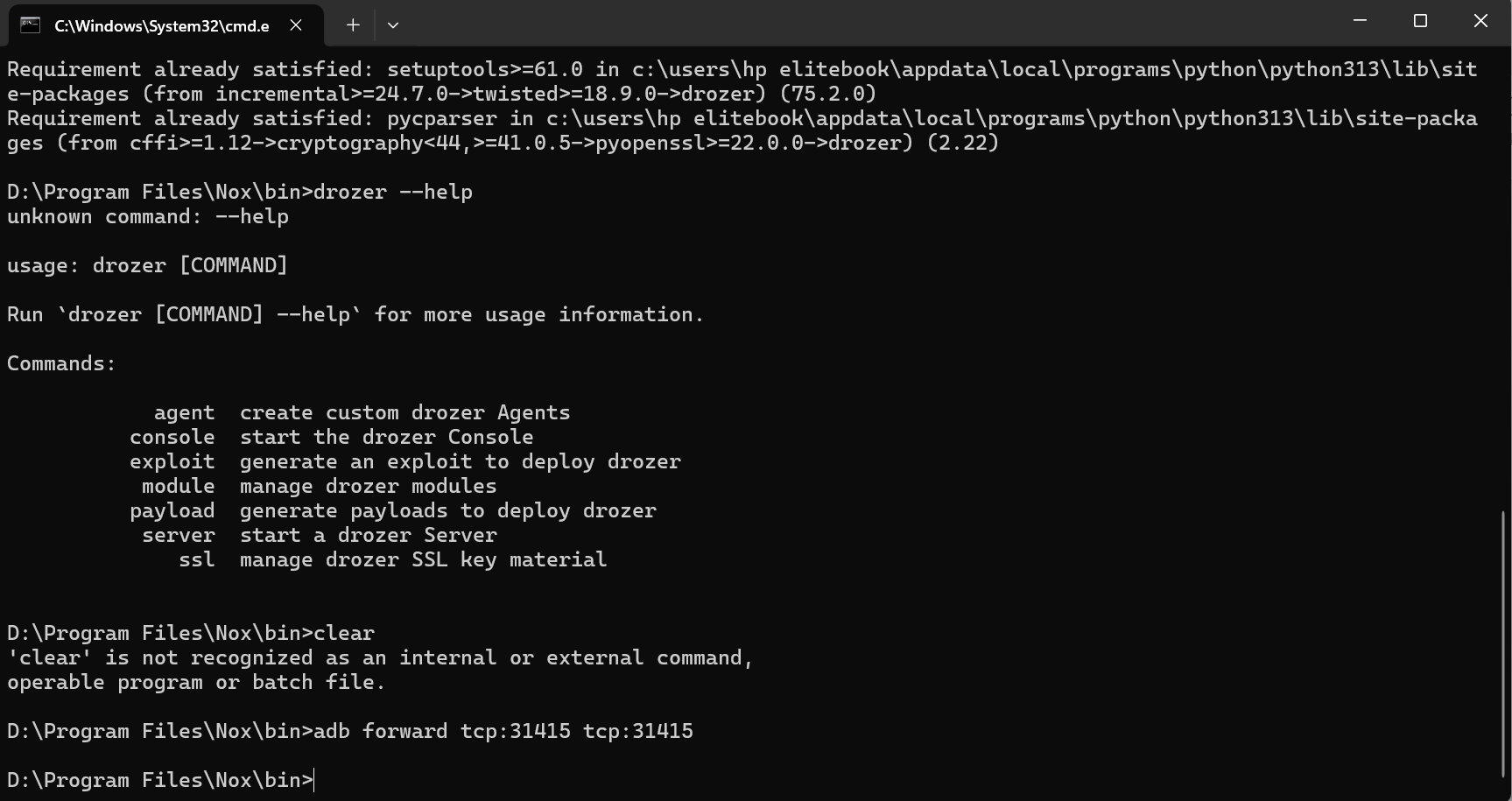
3. Verify Drozer Installation: Open command prompt and type the following commands to check if Drozer are installed and working properly:
“drozer –help”
4. Go to the Drozer GitHub repository: https://github.com/WithSecureLabs/drozer-agent/releases/.
5. Download drozer application for android.
6. Right-click on Nox Player and select “Open File Location” to navigate to the Nox Player/bin folder.
7. Open CMD in the Nox Player/bin path.
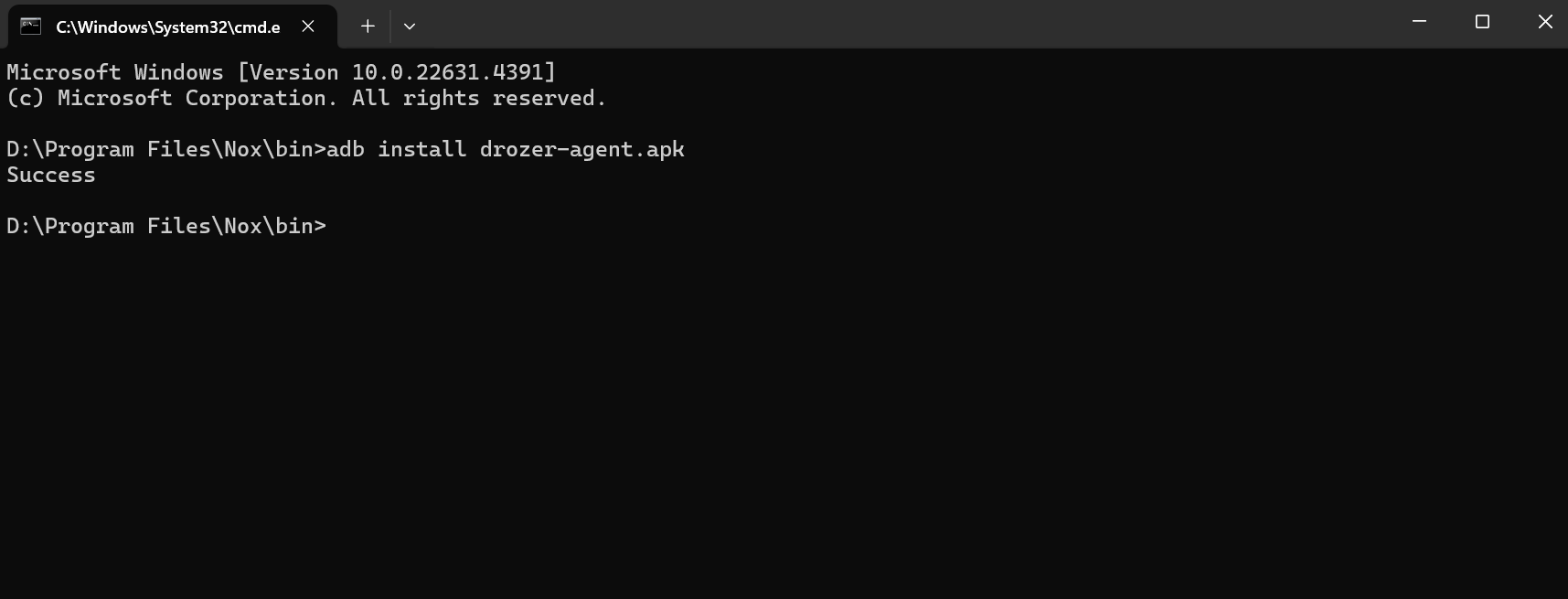
8. Install the drozer apk on emulator, run this following commands:-
“adb install <drozer-apk>”
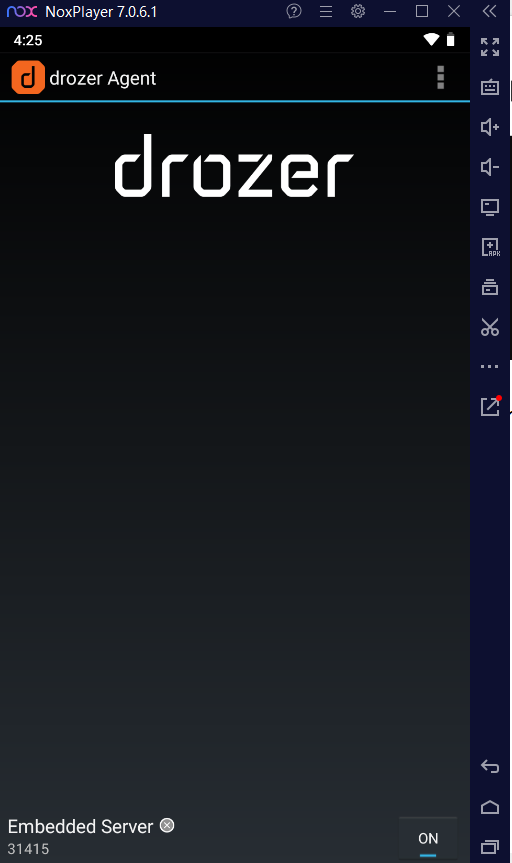
9. After installing Drozer, turn on the drozer switch.
10. After this run the following command for connection:
“adb froward tcp:31415 tcp:31415”
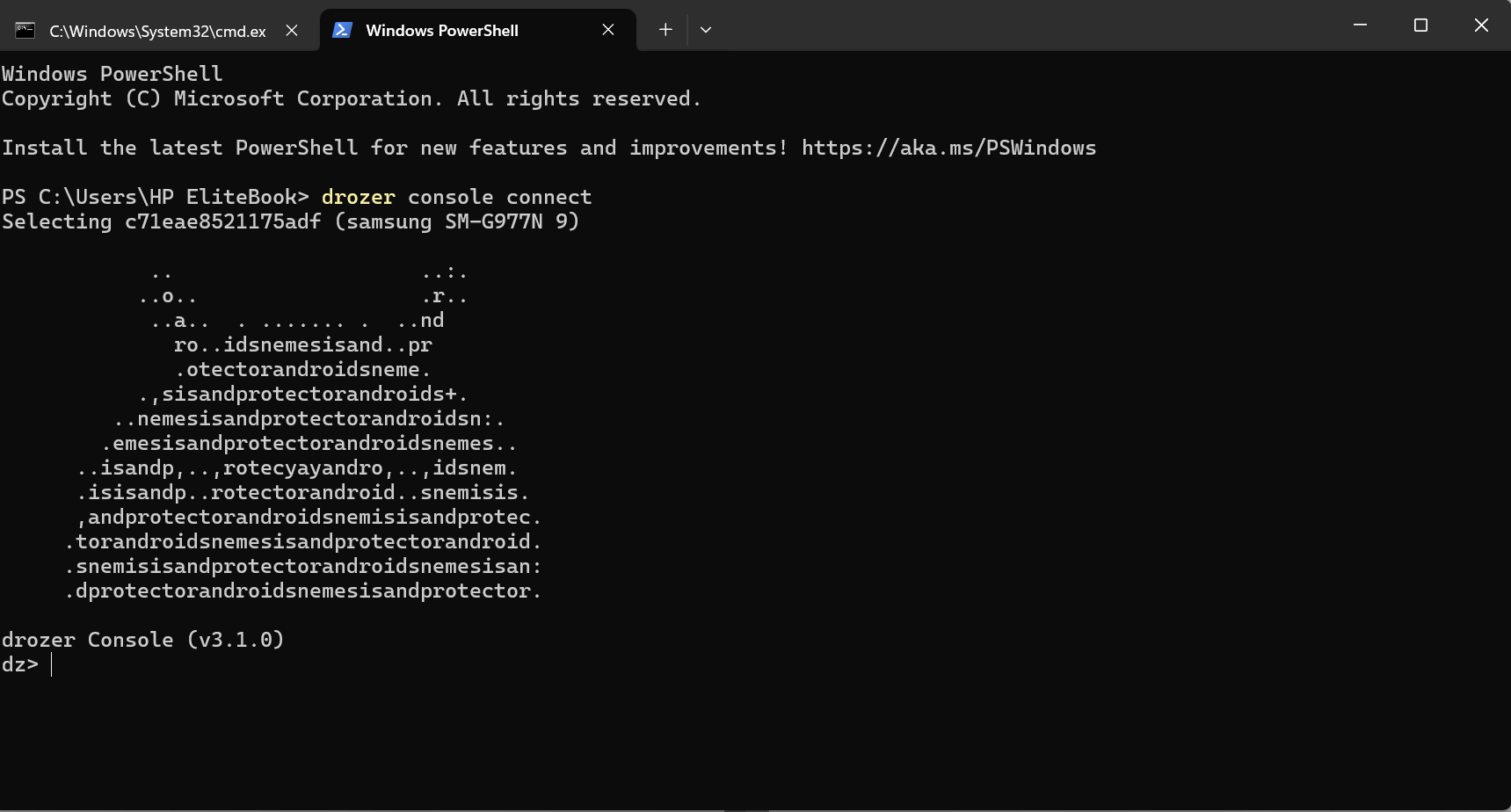
11. After this , Run this command for connect with drozer.
“drozer console connect”
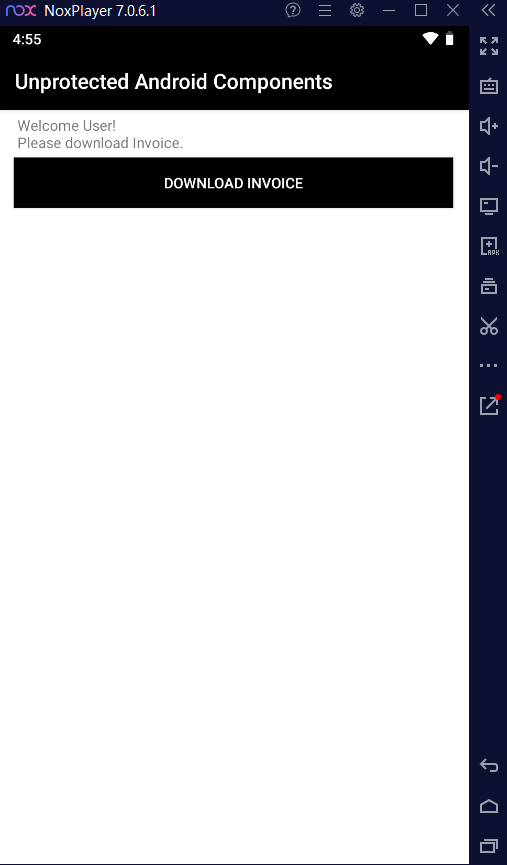
>> Here I am will demonstrate Drozer on vulnerable applications like:- Androgoat application.
1. First install the vulnerable applications:-
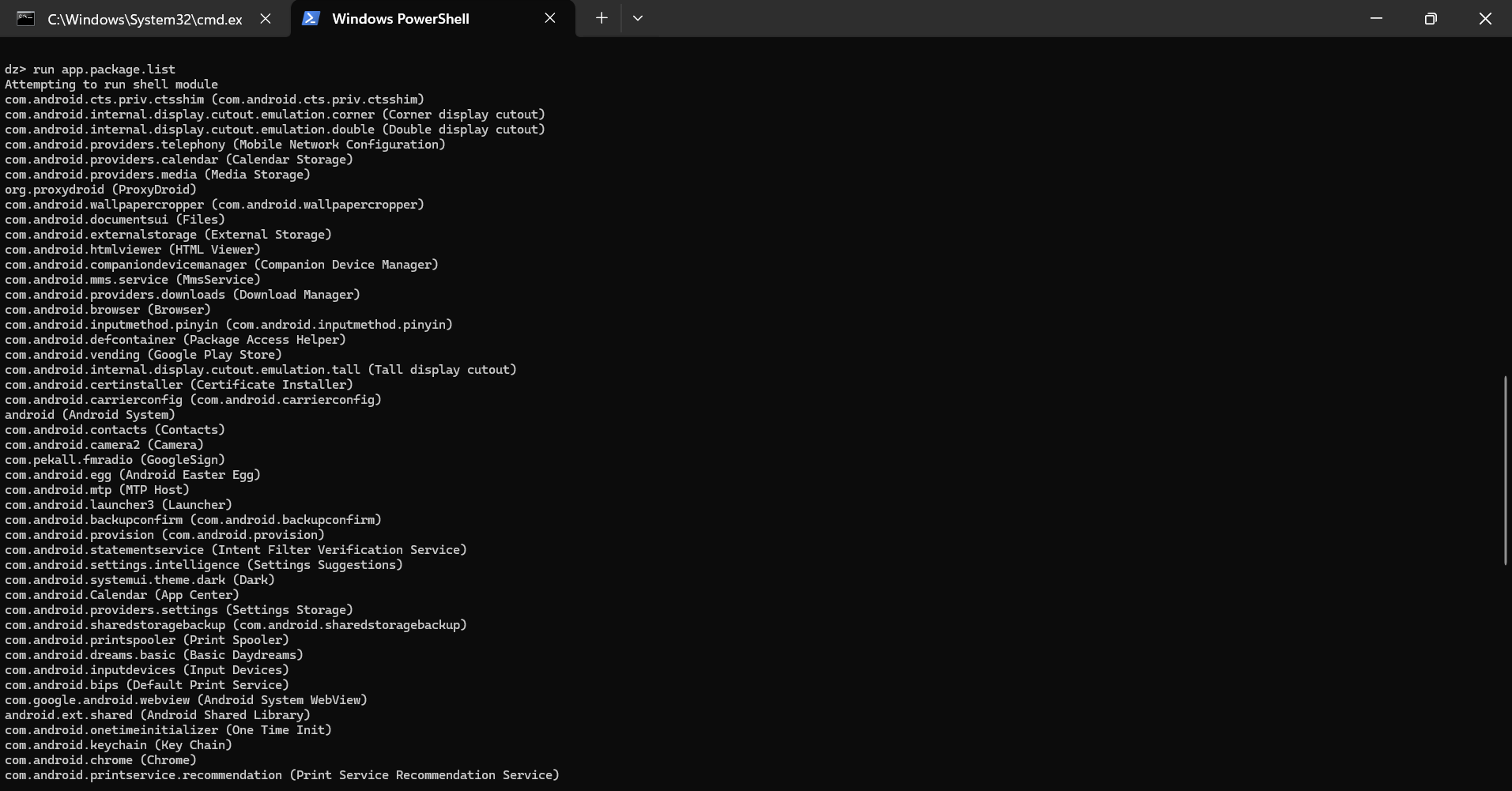
2. Let’s retrieve package name of all application on android:-
“run app.package.list”
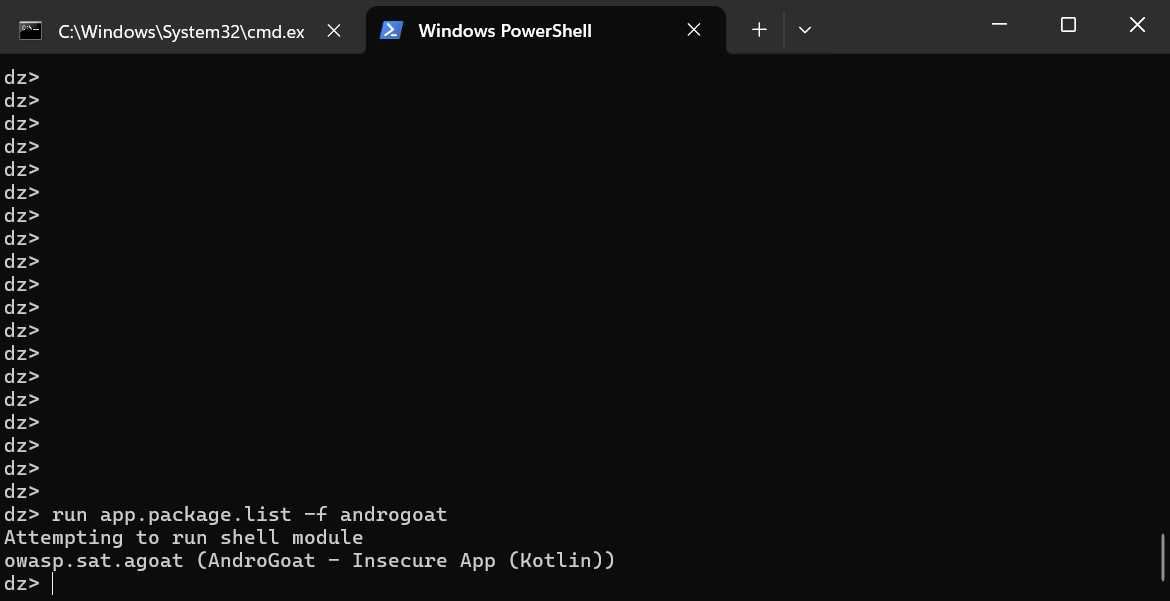
3. Let’s retrieve package name first of the vulnerable application.
“run app.package.list -f androgoat”
-f –> filtering package name
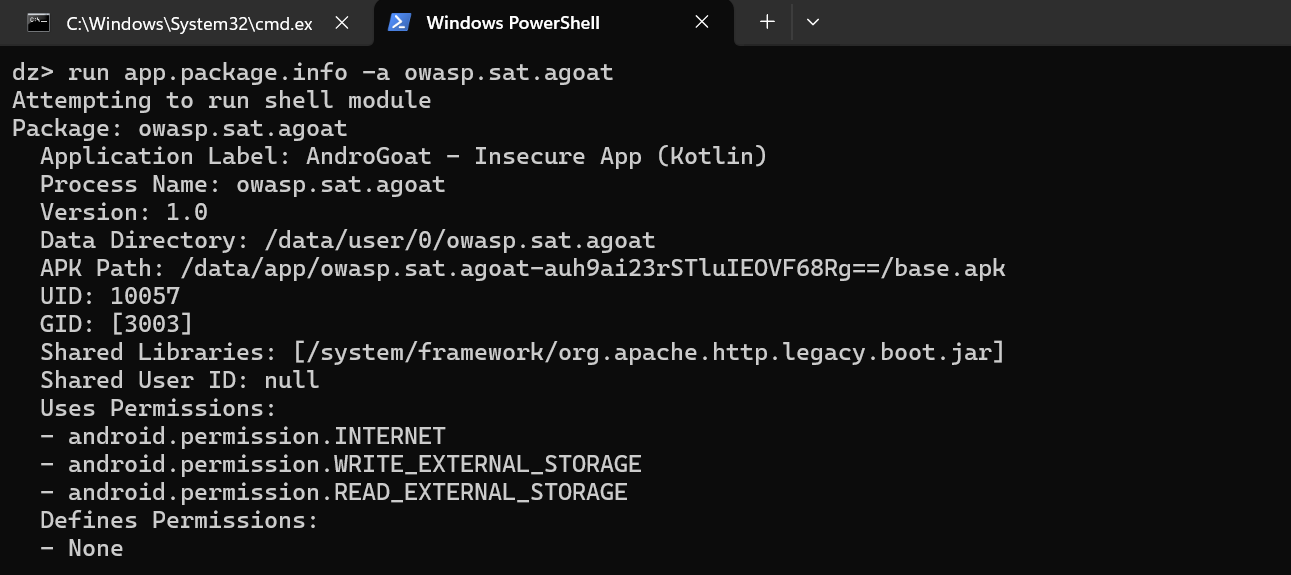
4. Let’s retrieve basic Information of the specific package name:-
“run app.package.info -a owasp.sat.agoat”
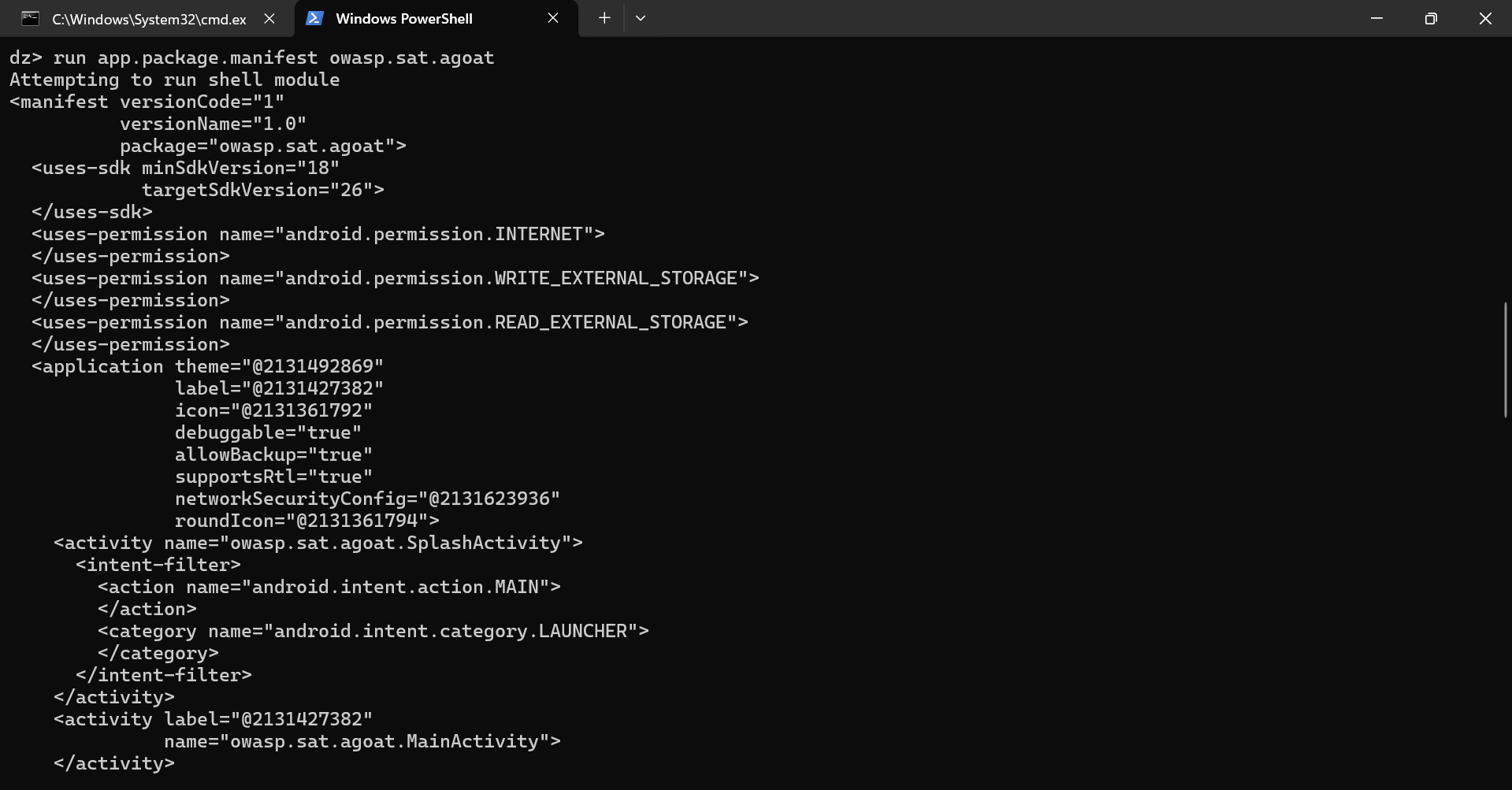
5. Now, we will read android manifest.
“run app.package.manifest owasp.sat.agoat”
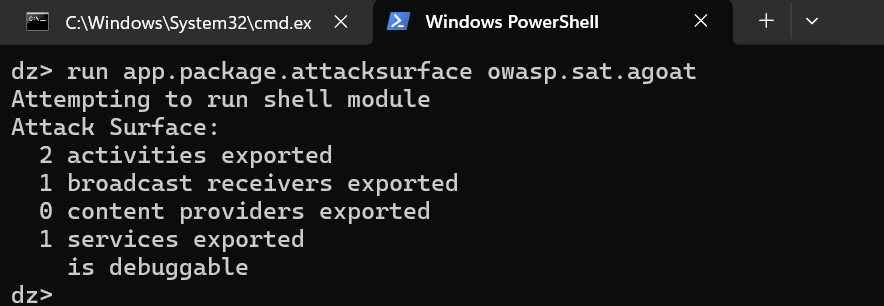
6. Now we will try to identify the attack surface of the application, run this following command in terminal:-
“run app.package.attacksurface owasp.sat.agoat”
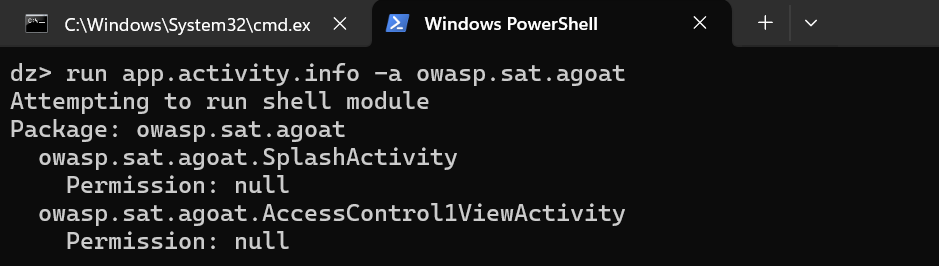
7. Let’s retrieve the exported activity component’s of the application.
“run app.activity.info -a owasp.sat.agoat”
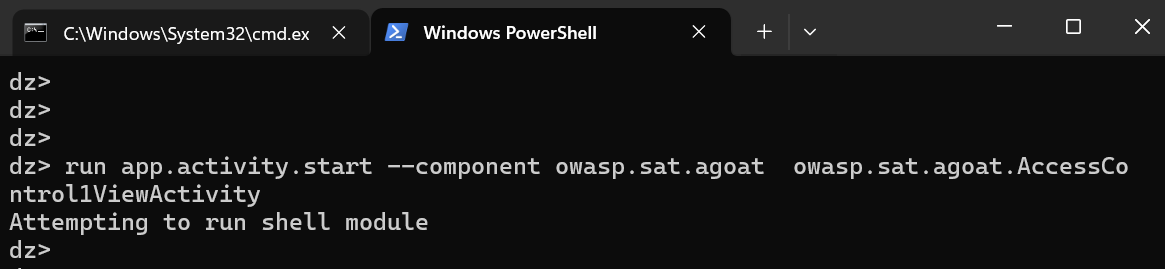
8. Now, Let’s try to exploit android activities. We are successfully exploit the activity.
“run app.activity.start –component owasp.sat.agoat owasp.sat.agoat.AccessControl1ViewActivity”
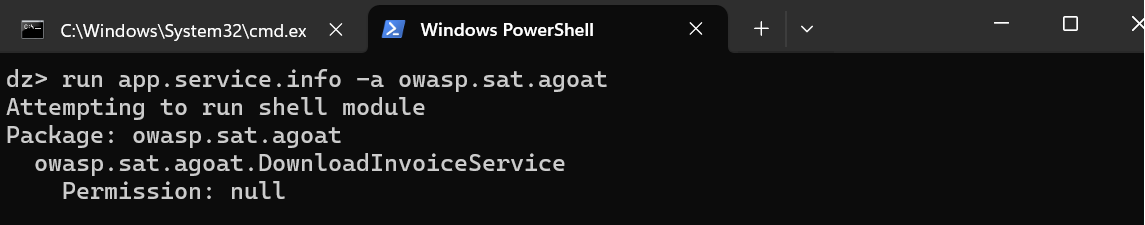
9. Let’s retrieve the services of android.
“run app.service.info -a owasp.sat.agoat”
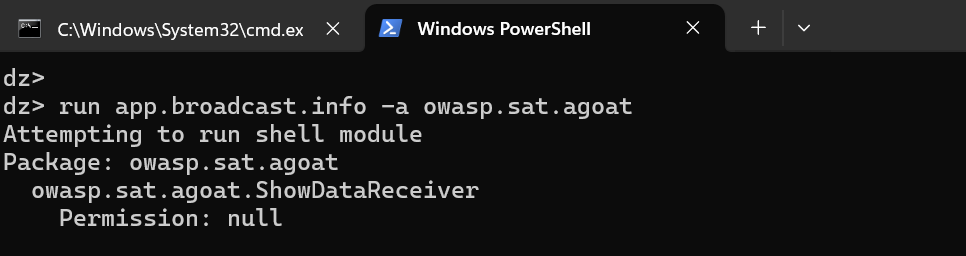
10. Let’s retrieve the all broadcast receivers.
“run app.broadcast.info -a owasp.sat.agoat”